Buffalo BS-GSL2024/2016P/2016 Series - Vulnerability Report
Product Description
The BS-GSL2024, BS-GSL2016P and BS-GSL2016 devices from Buffalo are business switches designed for medium and large organizations.

Affected Products:
All Buffalo BS-GSL2024, BS-GSL2016P and BS-GSL2016 devices from version 1.10-0.03 and under.
Vulnerability Summary
[CVE-2023-26588] - Use of Hard-coded Clear text Password (CWE-798).
Buffalo BS-GSL2024, BS-GSL2016P and BS-GSL2016 series devices contain hard-coded, clear text credentials for a hidden debug user account. A malicious actor can extract hard-coded strings from the firmware image and have access to the hidden UI web page. This vulnerability affects all Buffalo BS-GSL2024, BS-GSL2016P and BS-GSL2016 devices from version 1.10-0.03 and under.
Improper Access Control (CWE-284).
[CVE-2023-24544] - Buffalo BS-GSL2024, BS-GSL2016P and BS-GSL2016 series devices are affected by an insecure design vulnerability due to an improper directory access restriction. An unauthenticated remote attacker can exploit this by sending a crafted URI that contains the path of the download and upload configuration file. A successful exploit could allow the attacker to extract the admin password from the configuration file then re-upload it to escalate privileges. This issue affects all Buffalo BS-GSL2024, BS-GSL2016P and BS-GSL2016 devices from version 1.10-0.03 and under.
Technical Walkthrough
Use of Hard-coded Clear text Password (CWE-798)
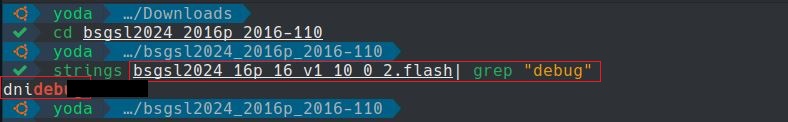
After extracting the firmware image and reverse
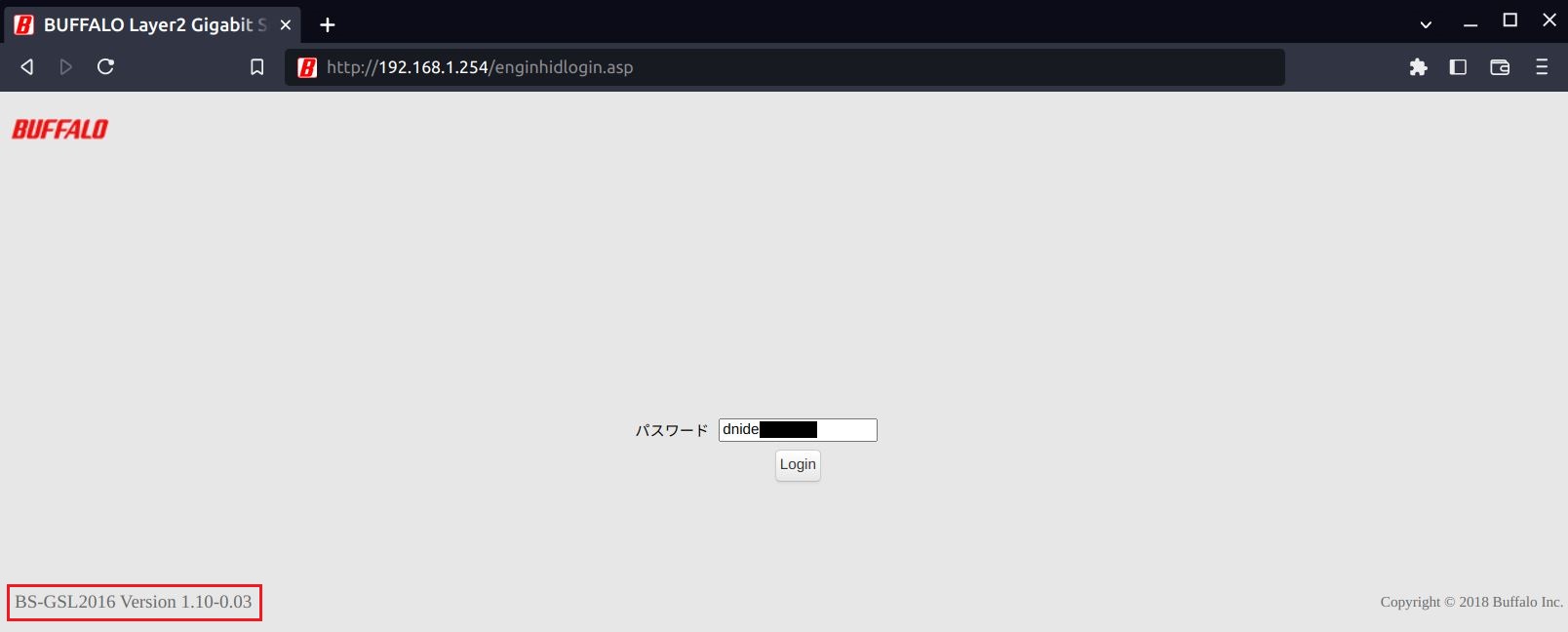
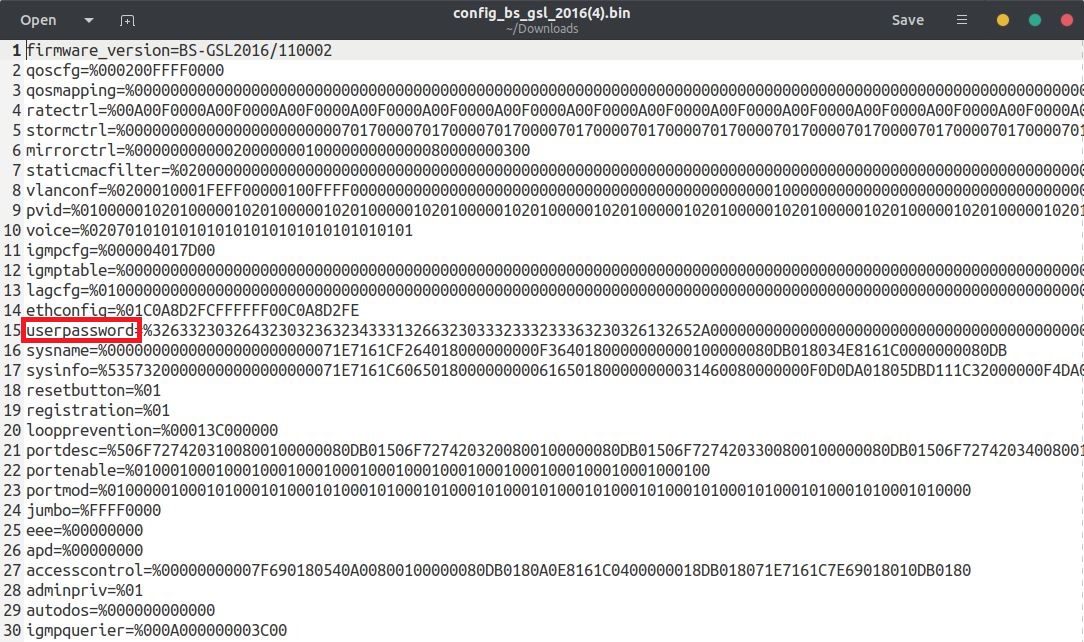
engineering it, it was discovered that the password to access the hidden
engineer page enginhidlogin.asp was hard coded in clear text in the firmware image.
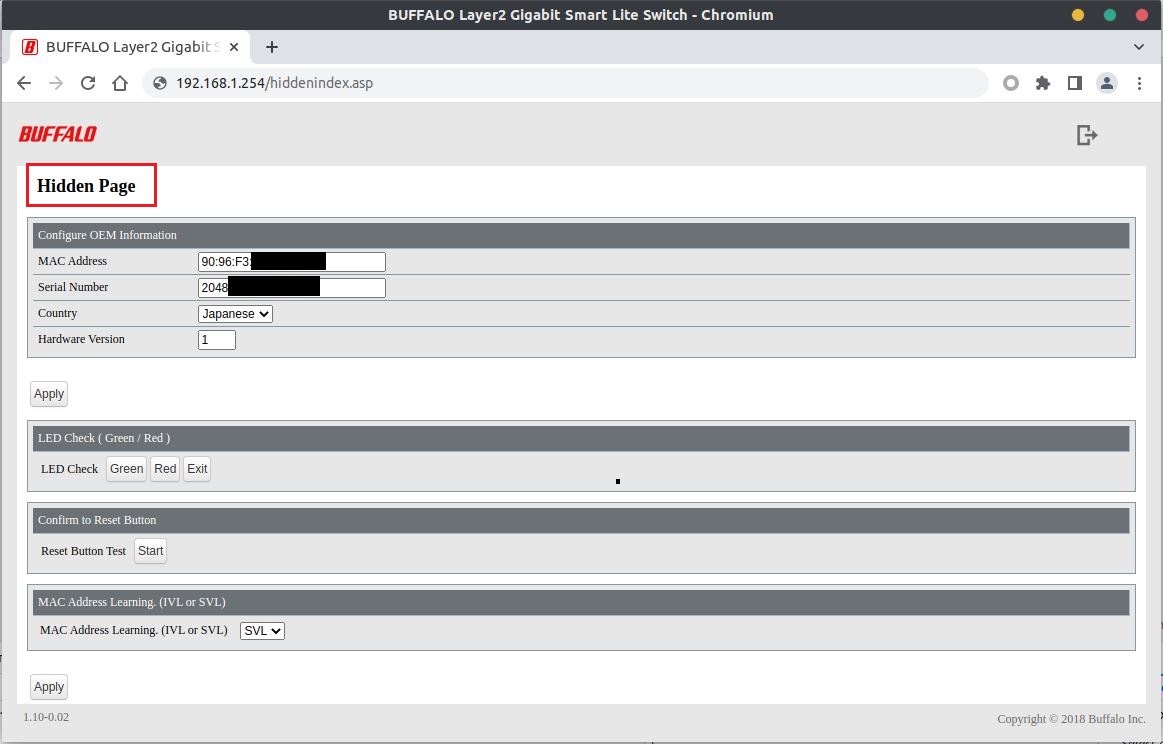
With this password, we can then access the hidden page at the endpoint hiddenindex.asp
Improper Access Control (CWE-284)
The endpoint /restore_conf.cgi can be called remotely without user authentication as there is no cookie verification for Cookie: BSGSL20XX=
to check if the request is legitimate. This vulnerability allows any
malicious actor the ability to download the configuration, modify it,
and ultimately re-upload it in the device to escalate privileges and
access the web UI interface.
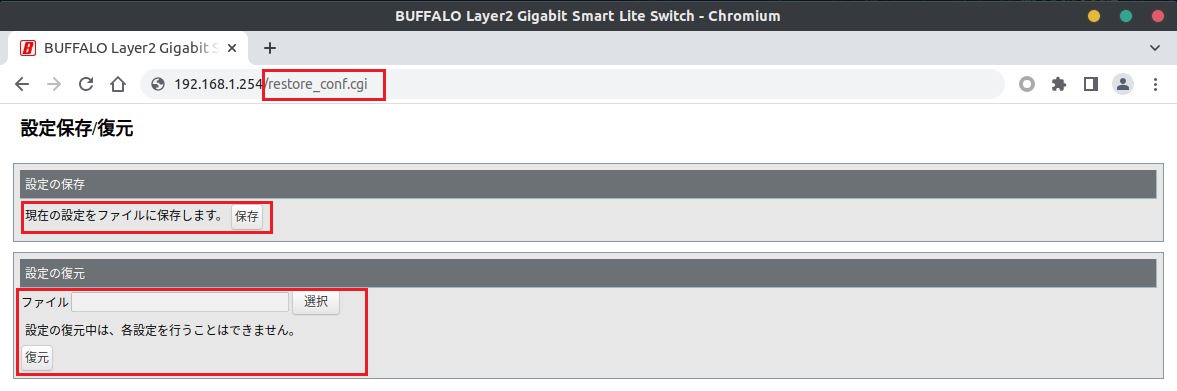
Configuration File
Recommendation Fixes / Remediation
Vulnerability 1: Need to generate a different password for each device. For example, a randomly generated, unique password should be generated for each device during the manufacturing process. Risk: Since passwords are shared among devices, an attacker would be able to crack the password once (e.g. with physical access to the device) and can then access all reachable devices. Please see the following link for more details: https://cwe.mitre.org/data/definitions/1188.html
Vulnerability 2: Make sure that all requests sent to the back end are authenticated properly. Please see the following link for more details https://cwe.mitre.org/data/definitions/284.html
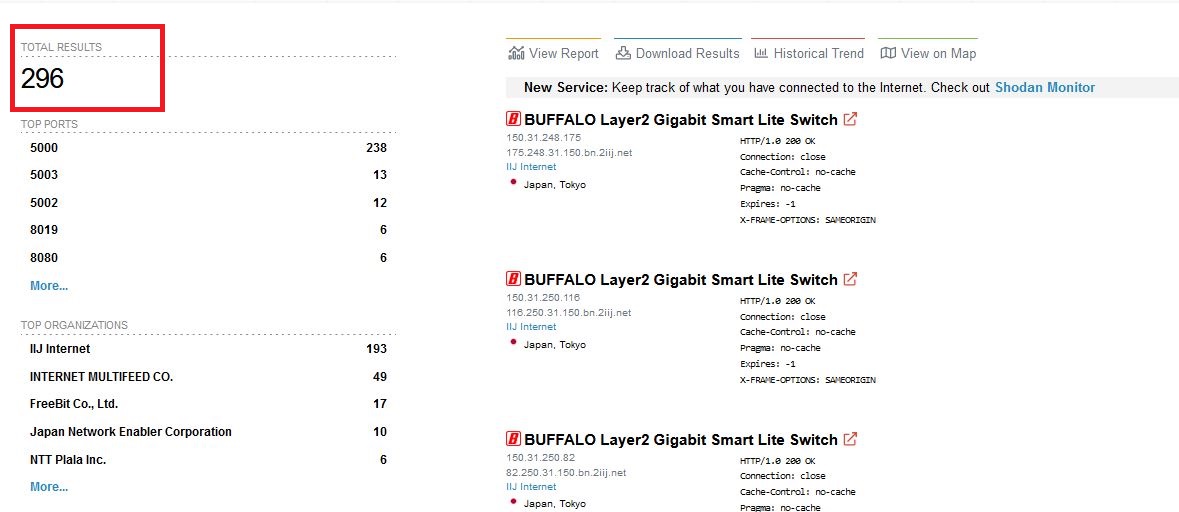
Vulnerable Devices Found
As of 19 Aug 2022, there were 296 Buffalo BS-GSL2024, BS-GSL2016P and BS-GSL2016 devices exposed to the internet and were affected by the vulnerabilities discovered.
Reference:
https://www.buffalo.jp/news/detail/20230306-01.html